Sponsored by CybelAngel
Sponsored by Cyberark
Secure Access and Enable Success for Your Workforce
Sponsored by Cyberark
The Hidden Gap in Web Application Security: User Sessions
Sponsored by Cyberark
Secure your transformational initiatives against modern security threats
Sponsored by Checkmarx
A Guide to Modern API Security
Sponsored by Checkmarx
Don’t Take Code from Strangers
Sponsored by Checkmarx
Application Security Testing Imperative in Modern Application Development: The Correlation
Sponsored by Checkmarx
10 Factors to Consider When Embedding AST into Your Pipelines
Sponsored by Digital.ai
How to Build a Blueprint for Secure Software (eBook)
Sponsored by Proofpoint
2022 State of the Phish
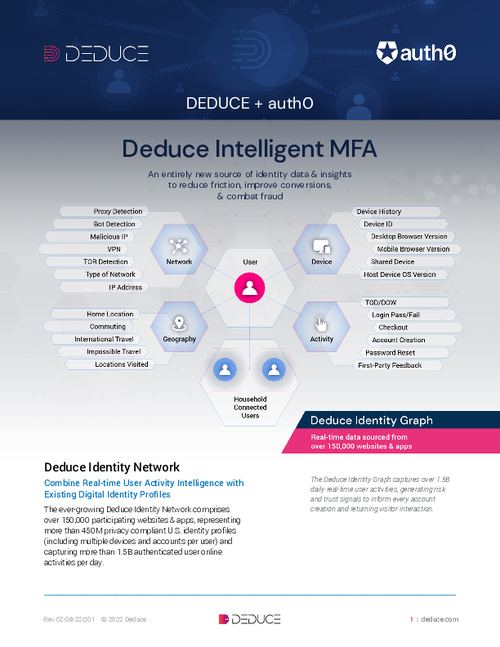
Sponsored by Deduce
The Ultimate Guide To Building A Trusted User Experience
Sponsored by Deduce
Stop More Identity Fraud With Intelligent MFA For Auth0
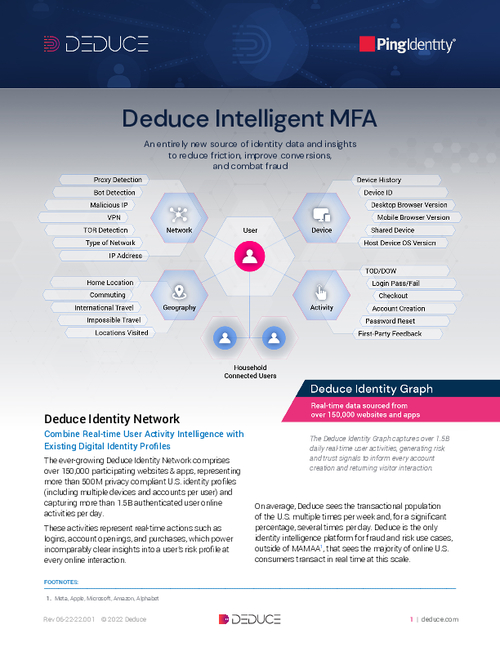
Sponsored by Deduce
Deduce Intelligent MFA For Ping Identity DaVinci Platform
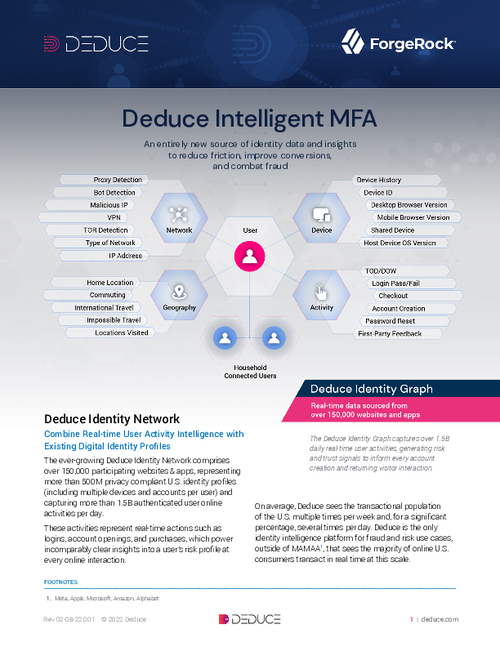
Sponsored by Deduce