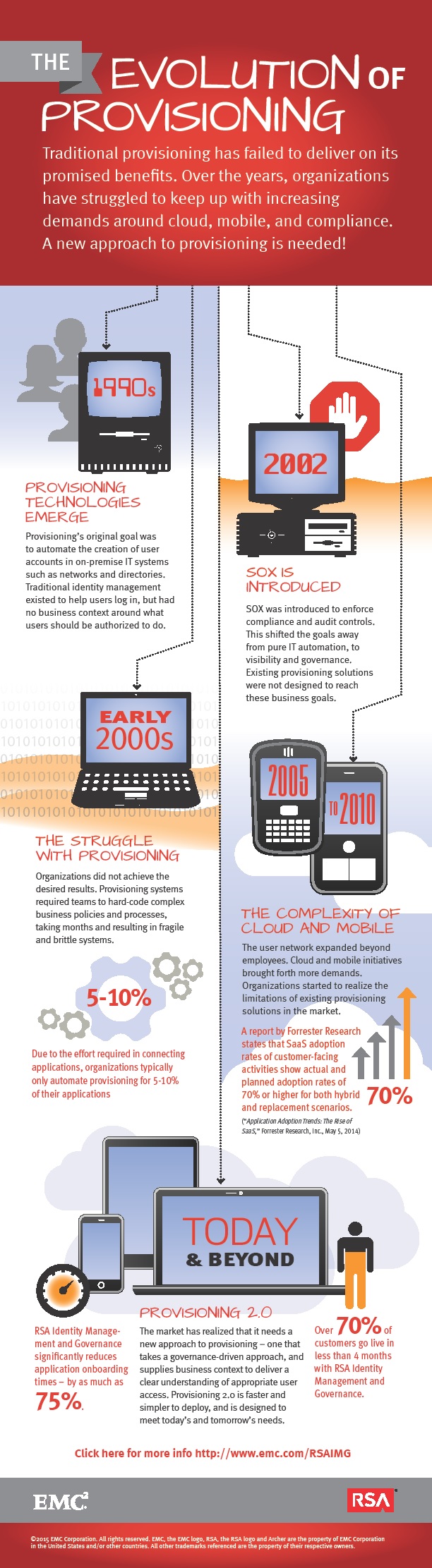
Sponsored by RSA
Sponsored by Dell
Using a Role-Based Approach to Permissions Management
Sponsored by Dell
Secure Your Data with Closed-Loop Identity & Access Governance
Sponsored by Dell
Identity and Access Management for the Real World: Identity Governance
Sponsored by Dell
Identity and Access Management for the Real World: Access Management
Sponsored by Dell
Get Ahead of Your Next Security Breach
Sponsored by Dell
IT Services Company Achieves Unified Access Governance For All Users
Sponsored by LifeLock
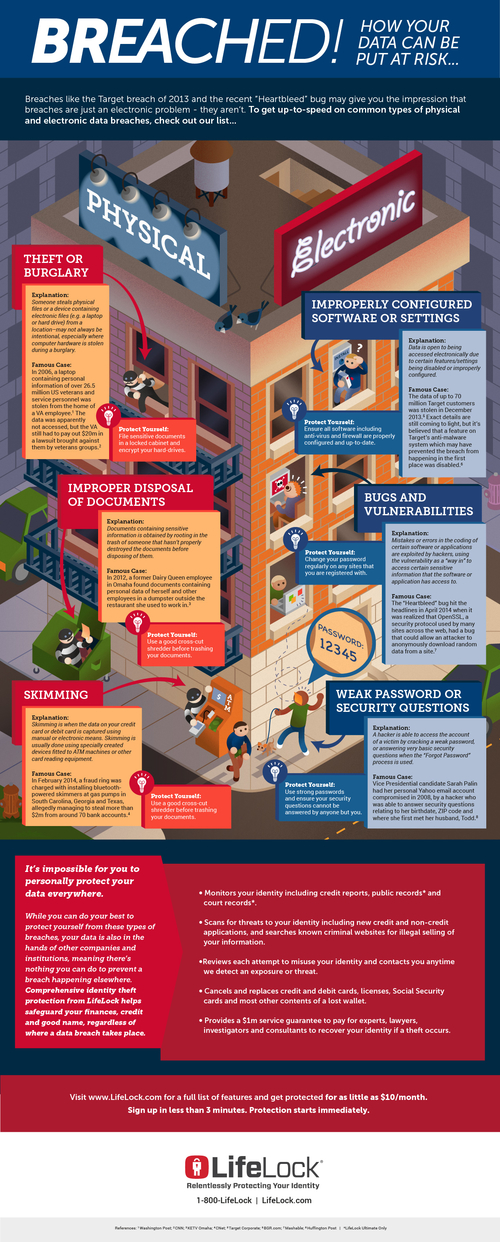
Breached: How Your Data Can Be Put at Risk
Sponsored by LifeLock
Combating Identity Fraud in a Virtual World
Sponsored by AlienVault
Practical Threat Management for Educational Institutions
Sponsored by AlienVault
Practical Threat Management for Government Entities
Sponsored by Alien Vault