Sponsored by Sophos
Sponsored by Radware
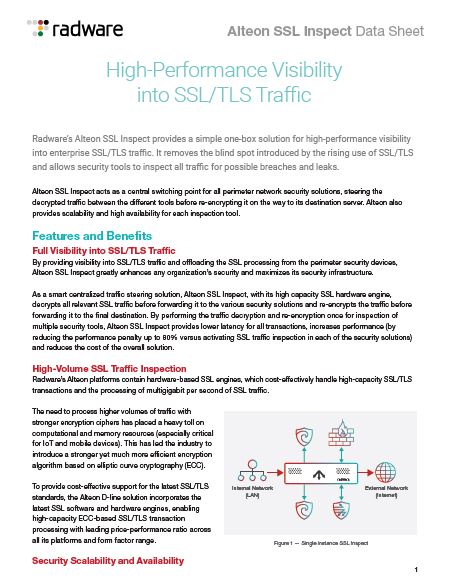
High-Performance Visibility into SSL/TLS Traffic
Sponsored by ForeScout
Total Visibility: The Master Key to Zero Trust
Sponsored by Optiv & Palo Alto Networks
The SASE Vision: Unifying Zero Trust, CASB & FWaaS
Sponsored by Zscaler
Four SD-WAN Security Hurdles to Overcome
Sponsored by Zscaler
Why IT Leaders Should Consider a Zero Trust Network Access Strategy
Sponsored by Hitachi ID Systems, Inc.
5 Questions Every CIO Must Answer in the Coronavirus Age
Sponsored by Zscaler
Network and Security Transformation - Enabling your Digital Business
Sponsored by eSentire
2020 eSentire Threat Intelligence Spotlight: United Kingdom
Sponsored by Gigamon
Why Zero Trust Is Critical to Federal Agencies
Sponsored by Gigamon
Implicit Trust No Longer Works. Here's How Healthcare Is Replacing It.
Sponsored by Gigamon
Network Visibility: The Enabler for Healthcare Innovation and Security
Sponsored by Rapid7
Choosing the Right Detection and Response Solution for your Business
Sponsored by Gigamon
ESG Brief: The Importance of a Common Distributed Data Services Layer
Sponsored by Expanse