Sponsored by Securonix
Sponsored by Guidepoint Security
SOC Modernization: Set Plays for Success
Sponsored by CrowdStrike
Adapt or Die: XDR Is On A Collision Course With SIEM And SOAR
Sponsored by Palo Alto Networks
Comprehensive and Proactive Security Operations for Financial Services
Sponsored by Splunk
Top 50 Security Threats
Sponsored by eSentire
RFP/RFI Sample Questions for Managed Detection and Response Providers
Sponsored by Splunk
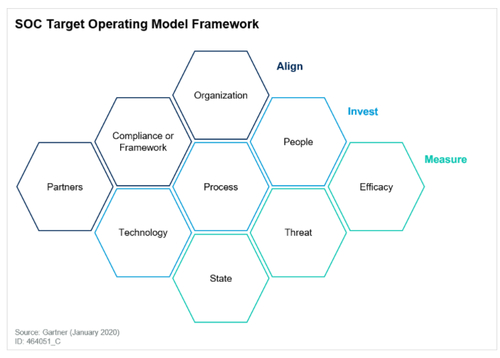
Gartner® Report: Create an SOC Target Operating Model to Drive Success
Sponsored by Graylog
What to Consider When Selecting a Source of Threat Intelligence
Sponsored by Cyrebro
Six Capabilities of a Complete SOC Solution
Sponsored by Splunk
Securing Complexity: DevSecOps in the Age of Containers
Sponsored by Vera, a Helpsystems Company
Definitive Guide to Bullet Proofing Data Security for Technology Companies
Sponsored by ServiceNow
ESG SOAR and MITRE ATT&CK
Sponsored by Splunk
The 10 Essential Capabilities of a Best-of-Breed SOAR
Sponsored by Splunk
The SOAR Buyer's Guide
Sponsored by Red Hat