Sponsored by Synchronoss
Sponsored by VMware AirWatch
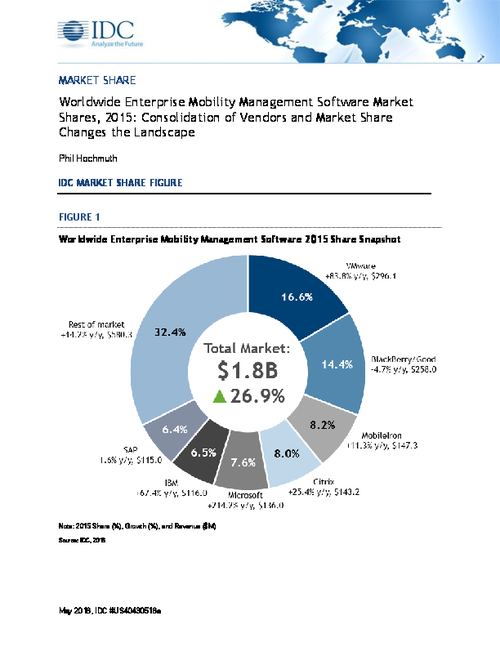
EMM Market Trends by IDC
Sponsored by VMWare
The Business Value of VMware Horizon
Sponsored by Hitachi ID
Best Practices for ID and Access Management (IAM) Implementation and Operation
Sponsored by Armor
How to Become HITRUST Certified
Sponsored by Armor
Case Study: HITRUST for HIPAA Compliance
Sponsored by Terbium Labs
Greatest Possible Cyber Protection for the Healthcare Industry
Sponsored by Palerra
Making Sense of the Shared Responsibility Model
Sponsored by Forcepoint
Superman or Superthreat? A Privileged User Risk Whitepaper
Sponsored by Palerra
The CASB Challenge: APIs or Proxies?
Sponsored by Pulse Secure
Pulse Policy Secure Solution Guide - Guest Access
Sponsored by Pulse Secure
Market Guide for Network Access Control
Sponsored by OneLogin
The Case for Cloud-Based IAM
Sponsored by iboss Cybersecurity