Stolen RDP Credentials Live On After xDedic Takedown
Customers of Notorious RDP Marketplace Expected to Move to Rival UAS Market
The notorious Russian language cybercrime marketplace and forum xDedic Marketplace remains offline following an international police takedown. But information security experts say customers will no doubt quickly move their business elsewhere.
See Also: Modernizing Malware Security with Cloud Sandboxing in the Public Sector
U.S. authorities estimate that xDedic, which was launched in 2014, helped contribute to more than $68 million in global fraud.
But the U.S. Department of Justice says that on Jan. 24, "seizure orders were executed against the domain names of the xDedic Marketplace, effectively ceasing the website's operation."
The takedown effort was international in its scope, reflecting the distributed infrastructure used by xDedic. The U.S. probe resulting in the seizure order was the work of the FBI and the Internal Revenue Service's Criminal Investigation unit. In parallel, a joint Belgian-Ukrainian investigation was led by Belgium's Federal Prosecutor's Office and the Federal Computer Crime Unit, together with Ukraine's National Police and Prosecutor General's Office. The EU effort was supported in turn by a Joint Investigative Team at the EU's law enforcement intelligence agency, Europol.
The German Bundeskriminalamt - the federal police, known as the BKA - also helped seize xDedic's infrastructure, authorities say.
Bitcoin Accepted
The xDedic forum has been a notorious source of stolen information and credentials, including remote desktop protocol credentials, which criminals can gather and sell to others who want to hack into a specific organization.
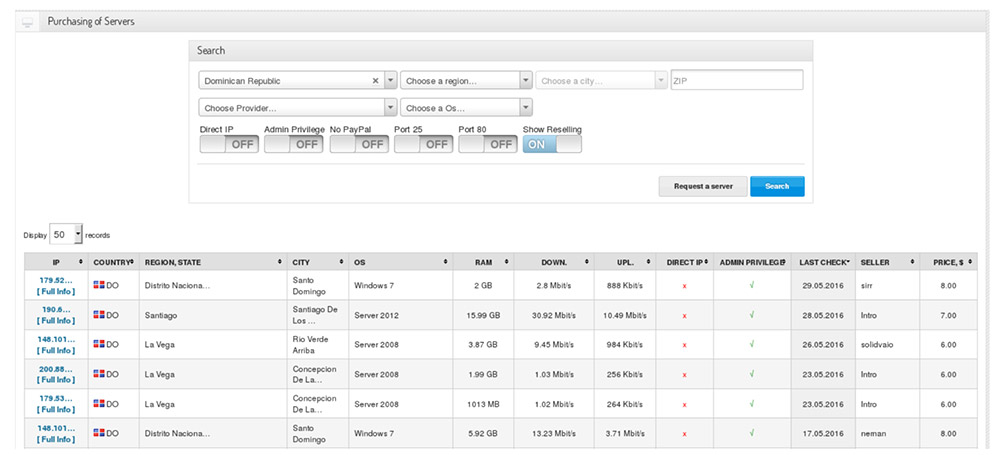
"Users of xDedic could search for compromised computer credentials by criteria, such as price, geographic location and operating system," Europol says."The xDedic administrators strategically maintained servers all over the world. Furthermore they utilized bitcoin to hide the locations of its underlying servers and the identities of its administrators, buyers and sellers."
Remote Access on the Cheap
RDP credentials have long been a cornerstone of the cybercrime economy. In June 2016, security firm Kaspersky Lab warned that 250,000 credentials for RDP servers around the world appeared to be for sale for as little as $6 each on xDedic (see: xDedic: What to Do If Your RDP Server Was Pwned).
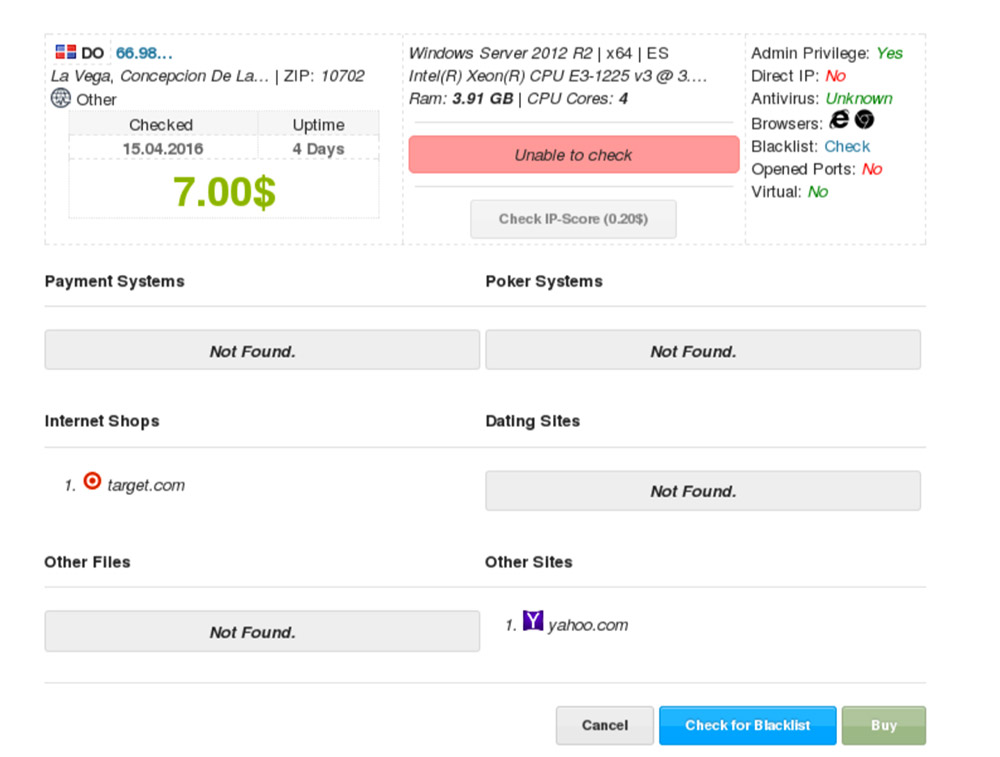
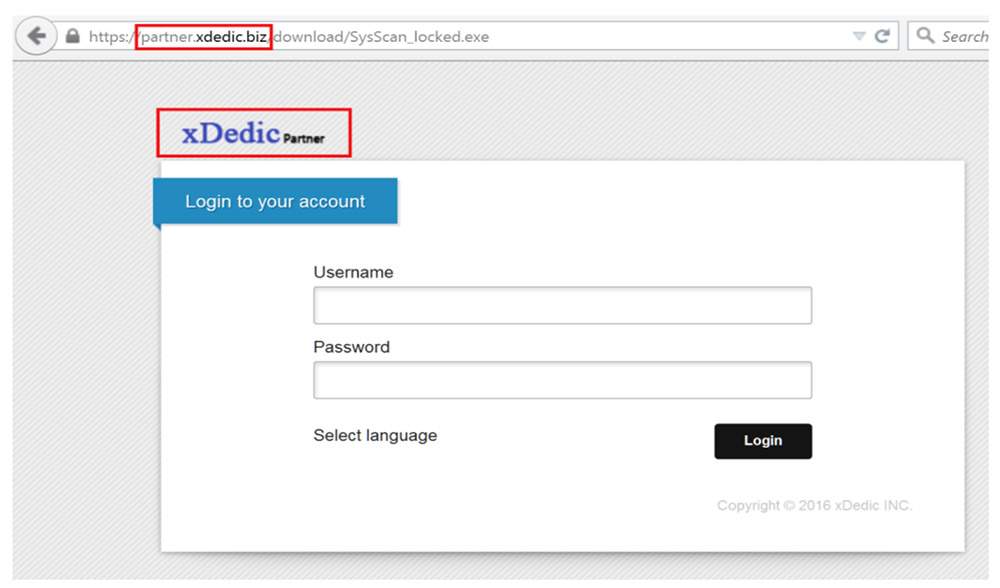
After that 2016 report was released, xDedic closed up shop and reopened as a darknet site, reachable only via the anonymizing Tor browser.
Vitali Kremez, director of research at threat intelligence firm Flashpoint, in April 2017 analyzed a publicly exposed dataset from xDedic that contained RDP access information for 85,000 servers. He found that the most compromised sectors were education, healthcare, legal and aviation. And the United States, Germany and Ukraine were the most targeted countries, based on the number of compromised RDP credentials contained in the data set (see: Hackers Exploit Weak Remote Desktop Protocol Credentials).
Europol says the credentials available for sale on xDedic could be used to gain remote access to organizations across numerous sectors, including "local, state and federal government infrastructure, hospitals, emergency services, major metropolitan transit authorities, accounting and law firms, pension funds and universities."
Kremez has said that investigators believe that The Dark Overlord, a hacker-extortion gang, regularly sourced RDP credentials from xDedic (see: Ransom Moves: The Dark Overlord Keeps Pressuring Victims).

Compared to the cybercrime market competition, xDedic's wares were typically more expensive, although it wasn't clear why, Flashpoint found. For example, in late 2017, the minimum price of a remote desktop protocol credential on xDedic was $10, while some sold for up to $100. That represented a significant premium compared to rival darknet market UAS - for "Ultimate Anonymity Services" - where RDP credentials sold for $3 and up (see: How Much Is That RDP Credential in the Window?).
Buyers Will Likely Flock to UAS
Guess where xDedic's customer base will likely now move?
"We suspect UAS will take over the RDP marketplace, solidifying its standing as the pre-eminent RDP shop, given that its main competitor is out of business," Kremez tells Information Security Media Group. "That will lead to more profits for the cybercriminals running UAS and their affiliates as a result."
But Flashpoint has also been tracing a decline in the use of such forums and greater adoption of encrypted messaging apps, with Telegram especially popular among Russian-speaking cybercrime aficionados (see: How Much Is That RDP Credential in the Window?).
After AlphaBay and Hansa
That shift has been driven by ongoing police takedowns of cybercrime forums, which has included law enforcement agencies seizing lists of customers and then paying them a visit.
Last year, the FBI, Europol and law enforcement partners announced the seizure of both the world's two biggest darknet marketplaces: AlphaBay and Hansa.
The law enforcement takedown of AlphaBay occurred around July 4, 2017. In response, many users switched to Hansa.
Secretly, however, Dutch police had already seized control of Hansa on June 20, 2017. Police then monitored Hansa for one month before taking it offline.
"The Dutch police collected valuable information on high-value targets and delivery addresses for a large number of orders," Europol said in a statement at the time. "Some 10,000 foreign addresses of Hansa market buyers were passed on to Europol."
RDP Credential Harvesting Continues
But criminals' collection of RDP credentials continues. Tyler Hudak, the incident response lead at information security consultancy TrustedSec, says his firm continues to see breaches that trace to compromised RDP credentials.
To study the problem, for 9.5 days in November 2018, Hudak ran an RDP honeypot, consisting of a Windows 7 virtual machine with mostly default settings. "The system was named 'payroll,' with the only user on the system also named 'payroll' and a password of 'password.' The 'administrator' account was disabled, as is the Windows 7 default," he says in a blog post.
The system also had an open RDP server, which recorded more than 58,000 logon attempts, using 4,980 different usernames, over the nearly 10 days that the system was active.
Hudak said the first attacker attempted to exploit the system after accessing it via RDP installed ransomware, while the second and third attempted to establish persistence so they could return later or sell the ability to do so to others. "The second attacker did this by modifying the RDP server to allow multiple connections and nothing else - likely hoping the credentials they knew would be valid at a later date," he says. "The third attacker, however, was not taking that chance. Not only did they modify the RDP server, they added multiple users they could use to log in at a later time."
In other words, any firm using RDP should ensure that it is locked down and well monitored. "This honeypot was an excellent example of how dangerous it is to put an RDP server on the internet," Hudak says.






















