Cybercrime , Cybercrime as-a-service , Endpoint Detection & Response (EDR)
Ryuk and Sodinokibi Surge as Ransom Payments Double
More Sophisticated Gangs Increasingly Target Large Enterprises, Coveware Warns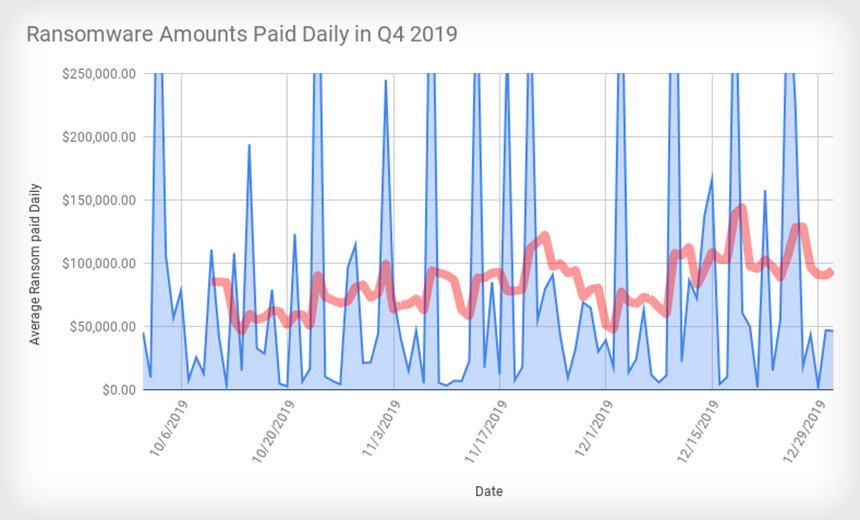
Bad news on the ransomware front: Victims are paying more money to criminals as attackers wielding two of the most prevalent strains target larger organizations.
See Also: The State of Organizations' Security Posture as of Q1 2018
So says ransomware incident response firm Coveware, based on cases in which it helped deal with infections in the fourth quarter of 2019.
The average ransom amount paid by a ransomware victim to their attacker - in exchange for the promise of a decryption tool - increased throughout last year. But from the third to fourth quarter of 2019, ransom payment amounts increased massively, from $41,198 to $84,116, Coveware reports. The median Q4 payment was $41,179.
"The doubling of the average reflects the diversity of the threat actors that are actively attacking companies," Coveware says in a new report.
Attackers using Ryuk and Sodinokibi - aka REvil - are increasingly "focusing their attacks on large companies where they can attempt to extort the organization for a seven-figure payout," it says, noting that the average Ryuk ransom payment last quarter was $780,000 (see: Ryuk's Latest Victim: Tampa Bay Times).
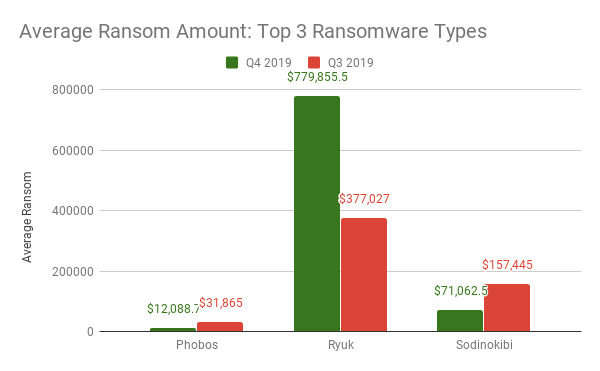
Sodinokibi last year seized the ransomware-as-a-service mantle from GandCrab after its developers announced they were retiring. The RaaS model involves developers taking a cut of every successful ransom payment received by their affiliates, who actively infect systems with a version of the ransomware that includes their unique affiliate ID (see: Sodinokibi Ransomware Gang Appears to Be Making a Killing).
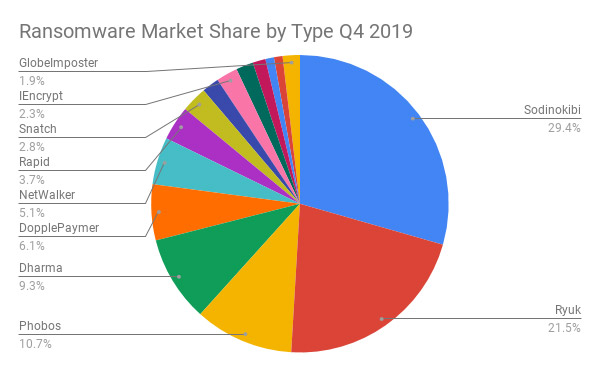
Sodinokibi was the most prevalent form of ransomware seen in Q4 2019, Coveware reports. Different affiliates may have different specialties, with at least one Sodinokibi ransomware affiliate specializing in hitting managed service providers.
Last year, a number of smaller RaaS variants also continued to target victims - especially small businesses. For these variants - including Dharma, Snatch and Netwalker - Coveware says attackers may demand as little as $1,500 for a decryption tool (see: Ransomware Attacks: STOP, Dharma, Phobos Dominate).
How do attackers get in? More than half of all ransomware outbreaks traced to attackers accessing organizations via weak or stolen remote desktop protocol credentials, 26 percent of attacks involved email phishing, and 13 percent traced to attackers exploiting software vulnerabilities, Coveware found (see: Ransomware Gangs' Not-So-Secret Attack Vector: RDP Exploits).
One commonality across all types of tools is that attackers overwhelmingly continue to demand ransom payments in bitcoins. Coveware says only about 1 percent of ransoms demand payoff in another digital currency, such as Dash.
Repeat Advice: Prepare, Don't Pay
The advice from security experts and law enforcement agencies continues to be clear: Prepare, don't pay. By maintaining up-to-date backups stored on disconnected systems, organizations can wipe and restore affected systems.
In some cases, organizations that fall victim to ransomware can make use of free decryptors, for example, via the public/private No More Ransom project. Some may also be able to tap cyber insurance policies to help cover costs.
Regardless of whether an organization recovers systems from backups or restores data by paying off attackers or using a free decryptor, outages may stretch to days or weeks.
"In Q4 of 2019, average downtime increased to 16.2 days, from 12.1 days in Q3 of 2019," Coveware reports. "The increase in downtime was driven by a higher prevalence of attacks against larger enterprises, who often spend weeks fully remediating and restoring their systems. Established enterprises have more complex networks, and restoring data via backups or decryption takes longer than restoring the network of a small business."
When victims do pay attackers for the promise of a decryption, in Q4 2019, 98 percent received a working decryption tool, Coveware reports, noting that attackers wielding Phobos, Rapid and Mr. Dec ransomware strains "are known to consistently default after being paid." For organizations that received a decryption tool, overall they recovered 97 percent of their data, and lost 3 percent, Coveware reports, noting that Ryuk and Sodinokibi ransomware tends to that more reliably correctly encrypt - and thus can decrypt - data.
Less sophisticated gangs, however, may build tools that make errors when encrypting data, meaning that after they delete the original file, it may never be recoverable.
Sodinokibi Study: $38 Million in Demands
Coveware's research comes with a caveat: It's based on the firms that it has helped deal with ransomware infections, including sometimes negotiating with attackers to try and reduce their ransom demand.
But other security researchers have also charted the steep fees being demanded by many ransomware-wielding gangs.
Researchers at Dutch service provider KPN's security team, for example, say they were able to sinkhole and track the operations of multiple Sodinokibi affiliates for the past five months, identifying a total of 150,000 unique infections. They also traced back 148 samples, finding that they collectively demanded more than $38 million in ransoms, or $260,000 each.
But ransom demands varied markedly. If Sodinokibi attackers hit a single system, their average ransom demand was $48,000. But if they hit a network of systems, their average demand was $470,000.
KPN found that at least 500 new, unique systems are being encrypted by Sodinokibi actors daily, although some of those systems might have been security researchers' sandboxes. But it also saw massive spikes in infections, which traced to attackers having successfully hit a managed service provider, using it as a springboard to infect hundreds or thousands of PCs that the MSP manages. "Some of the attacks are on a huge scale, encrypting over 3,000 unique systems in one attack," the researchers say (see: Texas Ransomware Responders Urge Remote Access Lockdown).
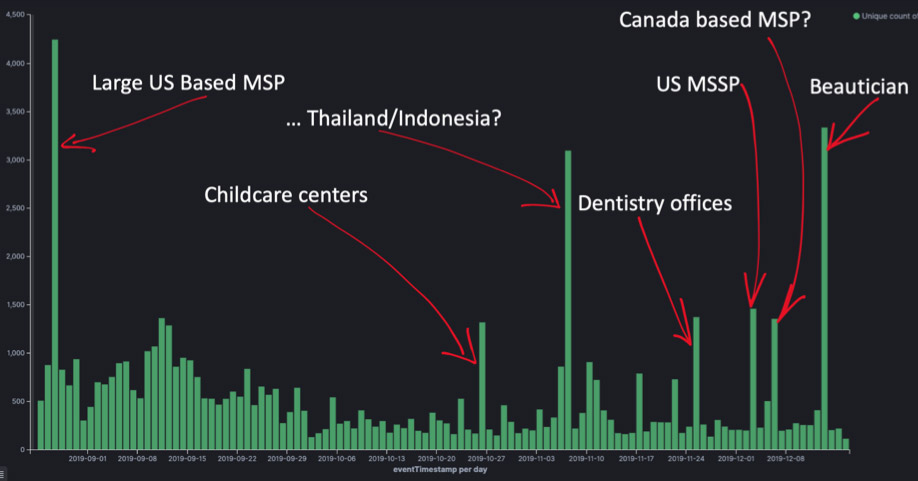
"Most of the peaks shown in the picture above hit the news," KPN says. "Other companies managed to keep the breaches out of the public, which is impressive as some of the attacks had a major impact on the affected businesses."
The researchers said they had difficulty ascertaining which ransoms got paid, because attackers used a different bitcoin wallet address for every victim who requests payment instructions.
Attack Sophistication Increases
But some more sophisticated attackers - including Ryuk users - have been adapting their efforts to better take down larger networks, researchers warn, to try and compel more victims to pay.
Ryuk attackers, for example, has been making use of the "wake on LAN" feature built into many types of computer hardware, which enables a computer to be activated even if it's powered off, as Bleeping Computer has reported.
As described by security researcher Vitali Kremez, who heads SentinelLabs, the research division of threat intelligence firm SentinelOne, Ryuk now includes the ability to scan ARP tables on an infected PC to obtain a list of known systems and their IP and MAC addresses. For any that are part of a private IP address range, the malware will then use wake-on-LAN to send a packet to the device's MAC address, instructing it to wake up, so it can be infected.
2020-01-12: #Ryuk #Ransomware | #Signed
— Vitali Kremez (@VK_Intel) January 12, 2020
[PET PLUS PTY LTD] #DigiCert
build: January 9, 2020
String Obfuscation
Same Wake-on-LAN (WOL) packet 172.16 & 192.168
Ref -> https://t.co/jdsR62ph0g
h/t @malwrhunterteam pic.twitter.com/6Ec9AK7bWc
Many systems may be powered down at night or over weekends, when IT staff are scarce. By powering them back on, Ryuk-wielding attackers can potentially crypto-lock more systems before security teams have a chance to mitigate the attack.






















