Endpoint Security , Governance & Risk Management , Open XDR
Researcher Finds Flaws in HP's Software Assistant Tool
Bill Demirkapi Says Software Is Risky With Unpatched Issues
Windows computers often come with a variety of software loaded by manufacturers. HP includes many tools, one of which underwent an unflattering examination by 18-year-old security researcher Bill Demirkapi.
See Also: Improving Security Compliance in The Financial Industry With Data Privacy Regulations
Demirkapi found 10 vulnerabilities, including three remote code execution flaws, within HP’s Support Assistant. The tool has been preinstalled on all Windows desktop and laptop computers HP has made since October 2012. It pulls system software updates and ones for drivers and utilities.

Demirkapi gained notoriety last year for finding vulnerabilities in education software made by Blackboard and Follett, as reported by Wired. His work garnered him a speaking slot last August at the DEF CON conference in Las Vegas, and he’s now a freshman at the Rochester Institute of Technology of New York.
He tells Information Security Media Group that HP’s Support Assistant is useful for a number of scenarios, but calls it bloatware, a subjective term for preinstalled software that can bother some users.
Remote Code Execution
In an extensive blog post, Demirkapi writes: “I always have considered bloatware a unique attack surface. Instead of the vulnerability being introduced by the operating system, it is introduced by the manufacturer that you bought your machine from.”
He sought to find a way to gain remote code exploitation and found a candidate in HP’s Download and Install Assistant, a component of HP’s Support Assistant. The goal was to avoid HP checking if the application has the correct signature so a malicious version of the application could be substituted.
He found three ways to gain remote code execution, one of which involved a victim performing two clicks after visiting a malicious website.
In a second example, Demirkapi got a signed HP binary to load a malicious DLL. A victim would only have to click once for an attacker to get remote access, although only the Arabic, Hebrew, Russian, Chinese, Korean, Thai or Japanese versions of the Download and Install Assistant work for that method.
The last method involves exploiting a very liberal acceptance of security certificates by HP. Demirkapi writes that the extension of a file is checked to see if it is an installer. If it is, the binary will be checked for HP’s signature. But the check only involves looking at the subject of the certificate and checking for variations on HP’s names, such as “hewlett-packard,” “hewlett packard” or “o=hp inc,” which could be easily spoofed.
“I could probably spend days making up company names,” Demirkapi writes. “All an attacker needs to do is create an organization that contains any of those words and they can get a certificate for that company. Next thing you know, they can have a one click RCE [remote code execution] for anyone that has the HP bloatware installed.”
Demirkapi also found five variations of local privilege escalation flaws and two ways to arbitrarily delete files. Although the file deletion issues don’t lead to local privilege escalation, he writes: “I felt that it was serious enough to report because I could seriously mess up a victim’s machine by abusing HP’s software.”
Seven out of 10 Patched
Demirkapi reported the flaws to HP in October 2019.
The remote code execution flaws have been patched. But only two of the five local privilege escalation issues have been completely resolved, leaving three outstanding, Demirkapi says.
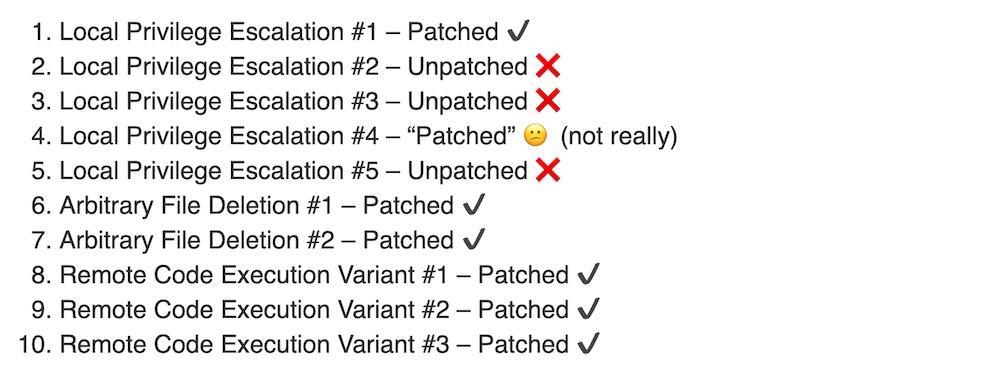
“Although I gave HP a 90-day time frame to patch the vulnerabilities, it has been six months since I reported them, Demirkapi says. “I didn't feel the need to ask them permission to disclose, though I gave a courtesy heads up.”
Whether users should leave the HP Software Assistant on their machine is a personal choice, Demirkapi says. But at minimum, users should ensure they have the latest version, which includes HP’s fixes.
“From a security perspective, HP Support Assistant is a security risk as long as it has outstanding vulnerabilities,” Demirkapi says. “It's up to the user to decide if the functionality of the product is worth more than the security risk.”
HP Responds
An HP spokesperson tells Information Security Media Group: “We were advised of potential vulnerabilities with some versions of HP Support Assistant and issued a security bulletin to address these. We are fully investigating any further vulnerabilities alleged by the researcher and will escalate any necessary mitigations. The security of our customers is always a top priority and we urge all customers to keep their systems up to date.”




















