3rd Party Risk Management , Cyberwarfare / Nation-State Attacks , Endpoint Security
Report: Huawei's Firmware Riddled With Problems
Huawei Has a 'Weak Security Posture,' Cybersecurity Firm Contends
(This story has been updated.)
See Also: 2018 Vulnerability Review: Evolution of Software Security From a Vulnerability Perspective
The firmware of more than 500 Huawei networking products is riddled with security weaknesses that make the vendor risky to use for next-generation 5G mobile networks, according to Finite State, a company specializing in internet of things security.
Finite State says it undertook a large-scale examination of Huawei’s code to contribute to the debate over whether the China-based vendor poses a risk. Several countries, including the U.S., Australia, New Zealand and Japan, have taken certain steps toward banning Huawei products.
“Many of these policy conversations have been missing a key set of ground truth facts, so we have set out to provide that,” says Matt Wyckhouse, Finite State’s co-founder and CEO, in a video. “In short, we’ve concluded that Huawei devices have a weaker security posture than other brands, and there are significant security risks associated with using these devices.”
Because there are just a handful of 5G vendors, there’s concern among Western governments that pervasive use of Huawei equipment could be leveraged by Chinese intelligence. Additionally, the next wave of innovation – from autonomous vehicles to telecommunication - will depend on the fast 5G networks, fueling worry about too much reliance a few vendors.
Huawei officials couldn’t immediately be reached for comment on the report. But Huawei has denied that it aids the Chinese government in espionage efforts and says that the security of its products is a priority.
’Poor Security Decisions’
Finite State’s 55-page report takes Huawei engineers to task for poor design decisions, deceptive labels in its code and leaving potential backdoors that could be exploited.
“Despite claims of prioritizing security, we quantitatively demonstrate that Huawei engineers systematically made poor security decisions in building the devices we test,” Finite State contends.
For its analysis, Finite State used a tool it developed called Iotasphere. The company says the tool contains dozens of “unpackers,” which can break down monolithic binary firmware images into components for analysis.
“As files are unpacked from a firmware image, they are processed by a series of file-level analysis modules,” according to the report. “These modules perform static, dynamic and symbolic analysis on files as they pass through stages of the analysis process.”
Finite State analyzed 9,936 firmware images in 558 of Huawei’s enterprise networking products. The report says researchers found hundreds of instances of potential backdoors, where improper default configurations could allow covert access to a device.
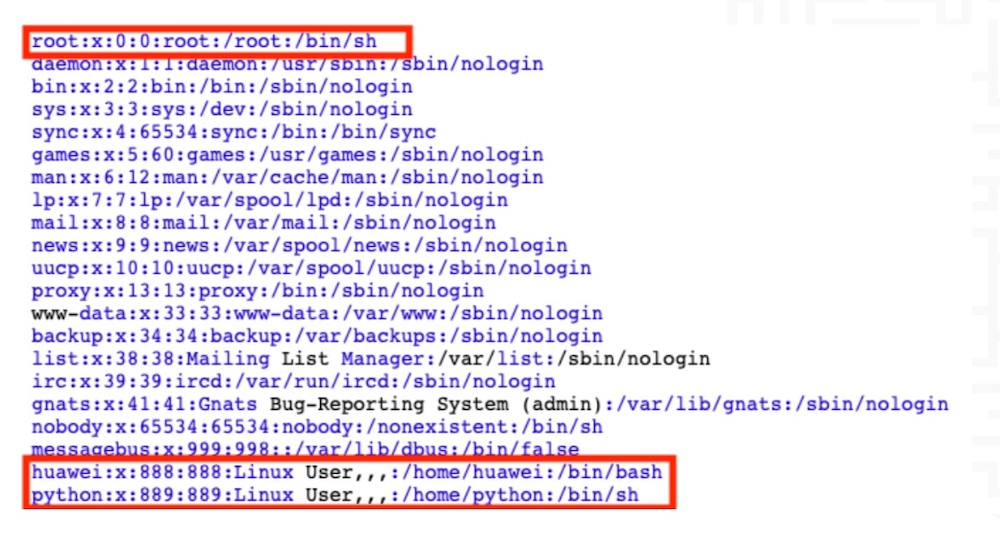
“These vulnerabilities manifested in the form of hard-coded, default user accounts and passwords, and several types of embedded cryptographic keys,” Finite State says.
It also found an average of 102 known vulnerabilities in the firmware images, often associated with third-party libraries or open-source libraries. The company says “a significant percentage” of those vulnerabilities were rated as high or critical.
One example cited is how Huawei employs the OpenSSL encryption library. Finite State found 79 versions of OpenSSL used across Huawei’s recent firmware releases. The oldest OpenSSL version discovered in a Huawei product was released in 1999.
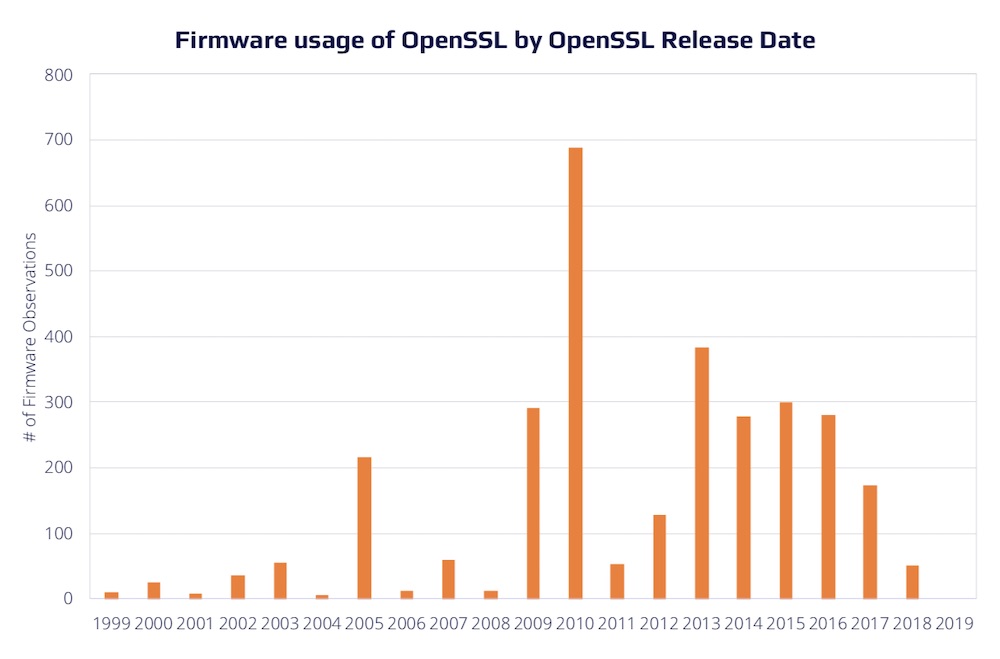
“In some cases, Huawei used 10-year-old versions of libraries containing dozens of vulnerabilities rather than selecting newer, more secure options,” the report says.
Researchers noticed other irregularities. For example, in some cases, the “memcpy” function was designated as the safe version, “memcpy_s.” But despite creating wrapper functions designated as safe, there were no safety checks, Finite State says. “This leads to thousands of vulnerable conditions in their code,” it says.
At Odds: U.S. and China
Huawei has sought to bolster confidence by setting up testing facilities for examination of its products. It has also said it will invest $2 billion over the next five years to make it networking equipment more secure.
“Despite what has been suggested in the media, there has never been a major cybersecurity incident involving Huawei, nor has anyone ever produced evidence of any security problems with our equipment,” the company wrote in a blog post in February. “Huawei is the most audited and inspected company in the tech industry.”
U.S. officials have expressed concerns about the company’s relationship with the Chinese government. But no public technical evidence has been released to support possible collaboration for espionage. Huawei has said it believes the accusations are intended to undermine its commercial position in 5G technology.
In the broader picture, Huawei remains center stage in an ongoing trade confrontation between the U.S. and China
Last year, President Donald Trump signed an executive order that banned the U.S. government from using equipment from Huawei and ZTE, another Chinese telecommunications company. Then in May, Trump signed another executive order - thought to target Huawei - that bans the purchase in the U.S. of telecommunication equipment from nations deemed to pose a spying risk. Also, the Commerce Department restricted what type of U.S. components Huawei could buy (see: Trump Signs Executive Order That Could Ban Huawei).
Update: On Saturday, Trump said he was suspending the ban on United States companies’ supplying equipment to Huawei as he hopes to reach a trade deal with President Xi Jinping of China, according to news reports.























