DDoS Protection , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development
Mirai Malware Attacker Extradited From Germany to UK
Daniel Kaye Charged With DDoS, Blackmail Against Lloyds and Barclays Banks
Admitted Mirai malware mastermind Daniel Kaye, 29, has been extradited from Germany to the United Kingdom, where he faces charges that he launched cyberattacks against two of Britain's biggest banks.
See Also: Infographic I NGINX 101
Kaye, a British national from Surrey, England, returned to Britain Wednesday in the custody of officers of the National Crime Agency - Britain's national law enforcement agency - under a European arrest warrant.
He's been accused of "using an infected network of computers known as the Mirai#14 botnet to attack and blackmail Lloyds Banking Group and Barclays banks," according to the NCA.
The bank attacks, which occurred in January 2017, led to the disruption of Lloyds Banking Group services, while Barclays managed to fend off the assault against it, the NCA says.
Kaye is due to appear Thursday in Westminster Magistrates' Court in London to face nine charges against him under the U.K. Computer Misuse Act, as well as two charges of blackmail and one relating to possession of criminal property, an NCA spokesman tells Information Security Media Group.
Kaye has also been charged with having allegedly "endangered human welfare with an alleged cyberattack against Lonestar MTN," which is the biggest internet provider in the West African coastal republic of Liberia, which has a population of nearly 5 million, NCA says (see Liberia Latest Target for Mirai Botnet).
The NCA says it filed charges against Kaye following a complex investigation that involved assistance from Germany's BKA, the Federal Criminal Police Office of Germany.
"The investigation leading to these charges was complex and crossed borders. Our cybercrime officers have analyzed reams of data on the way," Luke Wyllie, NCA's senior operations manager, says in a statement. "Cybercrime is not victimless and we are determined to bring suspects before the courts."
PoodleCorp Dumped Mirai
Kaye has been charged with making use of low-tech, high-impact Mirai malware. The malicious code was originally built by an individual or organization called PoodleCorp to exploit the default usernames and passwords used by dozens of manufacturers' IoT devices. Last October, however, PoodleCorp dumped the Mirai source code online. Seemingly overnight, a number of other individuals or organizations - including Kaye - began running their own Mirai botnets.
Mirai-promulgated DDoS attacks included such victims as domain name server provider Dyn, which experienced a record-setting attack that led to sites such as Amazon, PayPal, Spotify and Twitter being disrupted.
Busted at Luton
Kaye, meanwhile, was arrested on February 22 at London-area Luton Airport by the NCA at the request of Germany's BKA (see British Cops Bust Suspected German ISP Mirai Botnet Hacker). In March, he was extradited to Germany.
Appearing last month at a court in Cologne, Kaye pleaded guilty to infecting 1.25 million Deutsche Telekom routers with Mirai malware. He also pleaded guilty to launching attacks designed to infect devices with Mirai malware for the purpose of selling stresser/booter services - aka distributed denial-of-service attacks.
"The aim of the attack wave was to take over the routers and integrate them into a botnet operated by the accused," the BKA said. "Access to the botnet was allegedly offered by the accused via the darknet for multiple attack scenarios, such as so-called DDoS attacks."
Suspended German Sentence
Last month, Kaye was given a suspended sentence - of one year and eight months - by the German court after he pleaded guilty to related charges, characterizing what he'd done as being "the worst mistake of my life," Agence France Presse reported.
Kaye told the court he'd targeted the Deutsche Telekom routers after being paid $10,000 to attack Lonestar MTN by one of its Liberian ISP rivals, AFP reported. Lonestar estimated that it suffered €2 million ($2.37 million) worth of damage as a result and had to instruct its subscribers to disconnect their routers, install a patch and then restart them.
But security experts say Kaye has also been tied to attacks launched by a hacker who has used the handles "Peter Parker," "Spiderman," "BestBuy," "Popopret" and "Spidr," and that he also appears to be the author of the remote-access Trojan and keylogger called GovRAT.
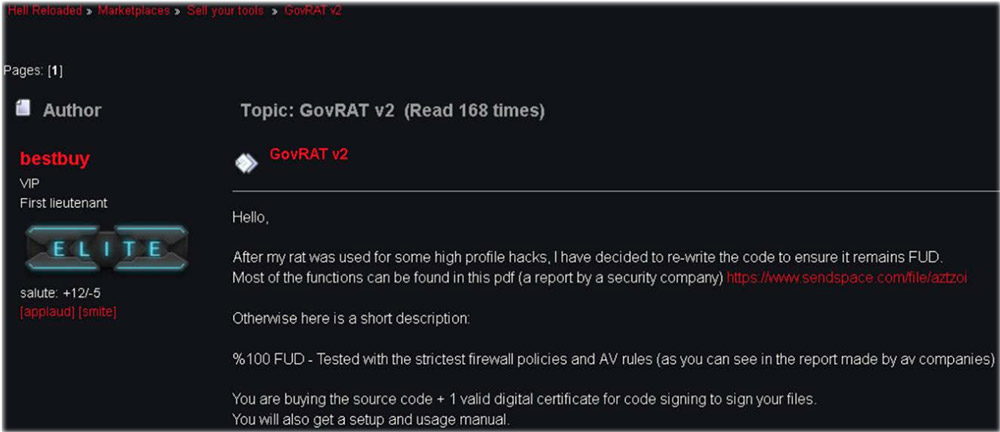
Security firm InfoArmor says GovRAT has been sold on darknet forums since 2014.






















