HIPAA Omnibus and Offshore Vendors
Will U.S. Regulators Enforce Actions Against Foreign BAs?
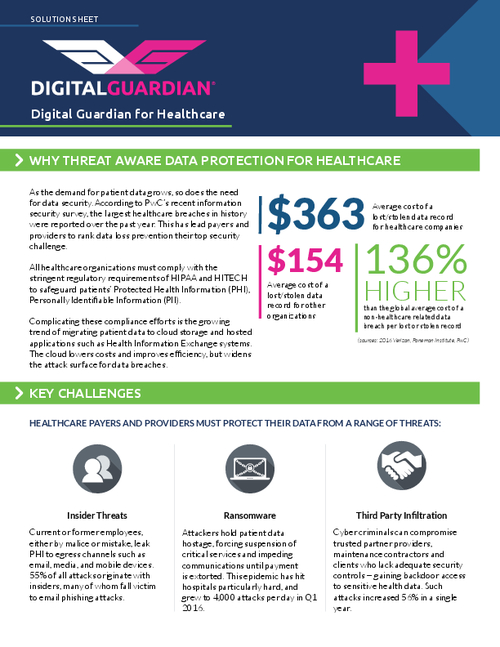
Under the HIPAA Omnibus Rule, business associates and subcontractors are directly liable for HIPAA compliance, including penalties for data breaches. And enforcement actions by federal regulators can range up to $1.5 million per HIPAA violation.
See Also: Embracing Digital Risk Protection: Take Your Threat Intelligence to the Next Level
But what happens if those vendors are located outside the U.S.? Will regulators still attempt to enforce compliance and penalties? These are among the questions healthcare organizations and their legal teams are asking as the Sept. 23 HIPAA Omnibus enforcement date nears.
"It's a mess. There's lots of uncertainty," says Kirk Nahra, a privacy and security attorney at law firm Wiley Rein LLP. "HIPAA doesn't say a word about offshore. But a BA is a BA is a BA."
Legal Considerations
The list of patient data-related services provided by offshore vendors to U.S. healthcare organizations "is pretty extensive," says Bob Chaput, CEO of security consulting firm Clearwater Compliance.
Those services include medical transcription, radiology readings, billing and clinical decision support.
But if there's a data breach involving one of those vendors, under HIPAA Omnibus, the ability for the Department of Health and Human Services to take enforcement action against offshore organizations falls into a gray area.
As a business matter, a foreign BA would be subject to a breach of contract claim should they violate their business associate agreement with a covered entity in terms of protecting patient data, says privacy attorney Adam Greene of law firm Davis Wright Tremaine. "It is untested, however, whether HHS has jurisdiction to bring in an [enforcement] action," Greene says. "HIPAA, unlike certain other federal statutes, does not have explicit extra-territorial reach."
There is also the practical reality that HHS may have limited resources to pursue a foreign BA, Greene notes.
If the HHS' Office for Civil Rights did choose to pursue action against an offshore BA, several questions must be considered. Among them:
-
If the breach involved a non-U.S. based subcontractor, did the covered entity or BA know that sensitive data was flowing there?
- Does the implicated offshore company have U.S. based operations, and what role (if any) did that unit have in the incident?
"If a company is in India, the Philippines, or elsewhere and it has no U.S. tentacles, but OCR wants to investigate a breach - this hasn't been explored yet," Nahra says.
Ultimately, OCR could put pressure on the covered entity to get the BA to cooperate, or simply scrutinize the healthcare organization's own HIPAA risk management and risk analysis practices.
"Each situation will have its own set of facts and a million different issues, including the relationship between the CE and the BA, the history," Nahra says. "There are risks with all BAs, and offshore just adds to that complexity."
Case Study: Cogent Healthcare
A recent breach hints of the complexity of offshore BA relationships. The principals: Cogent Healthcare, a covered entity headquartered in Tennessee, and M2ComSys, a vendor of medical transcription services. M2 is headquartered in India, but also has operations in Las Vegas. The company provided offshore and onshore medical transcription services to Cogent.
On Aug. 8, Cogent notified 32,000 U.S. patients that their data may have been improperly accessed when "a security lapse by M2 allowed some patients' PHI to be accessed through [an] Internet site," according to Cogent's public statement.
The breach involved patient care notes. "M2's job was to transcribe care notes dictated by physicians, such as when they discharged patients from the hospital," Cogent says. The unsecured access to these notes through the site began May 5, 2013, and ended following Cogent discovery of the lapse on June 24, 2013.
Since the discovery, Cogent has terminated its relationship with M2 and taken physical possession of hardware in use at M2's Las Vegas operations.
M2 officials did not respond to an inquiry by Information Security Media Group asking for comment.
A Cogent spokeswoman told Information Security Media Group that "M2 provided both onshore and offshore transcription services," to Cogent. However, when it comes to Cogent's own hospital clients, if specific contracts did not allow patient information to be communicated offshore, then Cogent used only onshore services, she says.
Still, because the Cogent breach involves a vendor that has operations in the U.S., any potential enforcement actions by OCR are potentially more clear-cut than if M2 had no U.S. presence at all.
"It's possible OCR could seek civil or criminal penalties in breaches that involve offshore companies with U.S. operations," says Chaput. "But if the company is totally offshore...you won't likely see OCR trying to prosecute a company in India or elsewhere."
"Regardless if they are domestic or offshore -- if the organization creates, receives, maintains, or transmits protected health information on behalf of a covered entity." says an OCR spokeswoman in a statement to Information Security Media Group.
"Business associates are directly liable under the HIPAA Rules and subject to civil and, in some cases, criminal penalties for making uses and disclosures of protected health information that are not authorized by its contract or required by law. Business associates are also directly liable and subject to civil penalties for failing to safeguard electronic protected health information in accordance with the HIPAA Security Rule," she says.
Advice for Covered Entities
So what steps should covered entities take if they rely on offshore vendors for services involving patient data?
Understand, first of all, that many offshore vendors are as good or even better than U.S. counterparts when protecting data, says Nahra.
"Dealing with a company in Pittsburgh doesn't mean security will be better than working with a company in the Philippines," he says. Many offshore companies, especially those that have a history in dealing with U.S. healthcare clients, are "very expansive and effusive" about their security, Nahra says.
In addition, "some foreign countries may have strong privacy and security protections in place comparable to [or even] more stringent than the U.S.," notes Greene.
In any case, breaches under HIPAA are predominately the burden of covered entities, regardless of where BAs are located. So, it's up to the covered entities to ensure their security, privacy and vendor management practices are sound.
"Hit first on risk management and good contract management practices," says security and privacy attorney Stephen Wu, a partner at Cooke Kobrick & Wu LLP. That includes conducting due diligence to find out where vendors operate, and whether those vendors subcontract to offshore contractors. Covered entities and their business associates "should know if downstream vendors are foreign entities," he says.
In addition, "covered entities should have a valid business associate agreement in place with these organizations to ensure that their business associates appropriately safeguard protected health information," says the OCR spokeswoman. "The business associate contract also serves to clarify and limit, as appropriate, the permissible uses and disclosures of protected health information by the business associate, based on the relationship between the parties and the activities or services being performed by the business associate," she says.
Nahra also reminds covered entities to provide all BAs only with "minimal necessary" data to perform the contracted service. "The problem is a number of BAs are given lots of sensitive information they don't need," he says.
Chaput advises covered entities to seek a copy of a BA's own security risk analysis, attestation of employee training, and reserve the right to perform a security audit of the vendor.
The reality for many covered entities, however, is that they don't have the bandwidth to perform all those check-ups on every BA, Chaput says.
In a worst case scenario, if a breach occurs, Chaput urges healthcare organizations to be proactive. "You can fire the BA and call OCR," he says.
What happens after that is still an open question.