DDoS Protection , Endpoint Security , Fraud Management & Cybercrime
Hacker Exploits Huawei Zero-Day Flaw to Build Mirai Botnet
Huawei Patches Flaw to Block 'Satori/Okiru' Variant of Mirai IoT Malware
An attacker has been attempting to infect hundreds of thousands of Huawei home routers with a variant of the notorious Mirai malware, security researchers warn.
See Also: Demonstrating HIPAA Compliance
On Friday, Huawei issued an updated security alert about the attacks, confirming that its range of HG532 home routers have an exploitable vulnerability. "An authenticated attacker could send malicious packets to port 37215 to launch attacks," Huawei says. "Successful exploit could lead to the remote execution of arbitrary code."
Beginning on Nov. 23, there was a sharp spike in attacks that aimed to exploit what was then "an unknown vulnerability in Huawei HG532 devices across the world, most notably in the USA, Italy, Germany and Egypt," researchers at Israeli security firm Check Point Software Technologies say in a recent blog post. Check Point first issued a public alert about the flaw last month, though did not reveal the precise vulnerability or how it could be exploited.
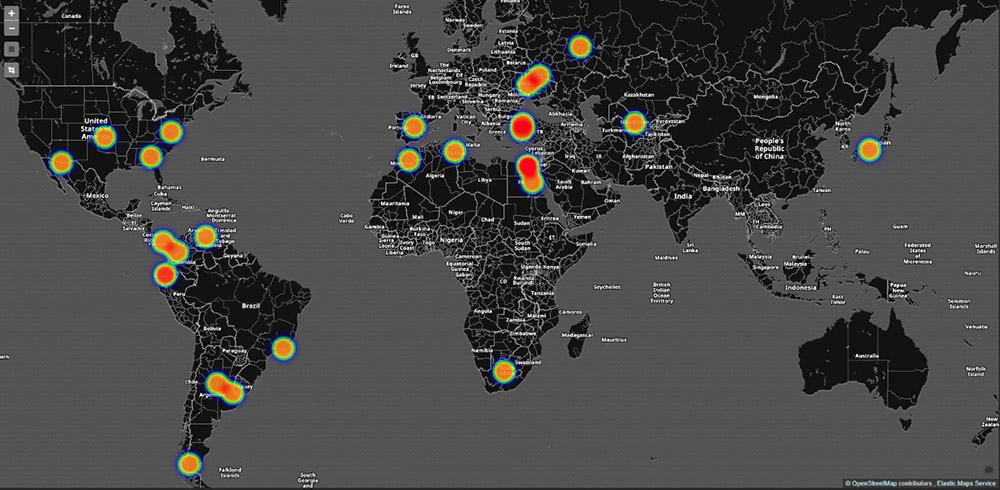
On Nov. 24, researchers at Chinese network security research firm Qihoo 360 Netlab reported seeing nearly 100,000 IP addresses just in Argentina tied to the attacks, and said they had been infected by a new strain of the "internet of things" Mirai malware that it called Satori, which is also known as Okiru (see The Next IoT Botnet Has Improved on Mirai).
Huawei says it was first notified about the flaw by Check Point researchers on Nov. 27, at which point its product security incident response team immediately launched an investigation, which remains ongoing.
Check Point says the flaw exploited in the attacks exists because the Huawei routers expose port 37215 to the internet. The port is used to implement the Universal Plug and Play - UPnP - protocol in the devices. "Designed and intended for local network configuration, [UPnp] in practice allows an engineer to implement basic device configuration, firmware upgrades and more from within the internal network," they say.
On Dec. 1, Huawei released intrusion prevention signatures that can be used - for example, by service providers to protect subscribers - to block any attempts to exploit the router vulnerability. Router users can also change their device's default password and enable the router's built-in firewall to block the flaw, the manufacturer says.
Huawei didn't immediately respond to a request for comment about how it is disseminating patches to affected users.
Security experts appear to have been able to sinkhole at least some of the command-and-control servers being used to send instructions to Satori-infected endpoints, blunting the attacks.
Malware Builds DDoS Cannons
Satori is based on the Mirai source code, security researchers say. "The payload is quite simple in its functionality," Check Point says. "The main purpose of the bot is to flood targets with manually crafted UDP or TCP packets."
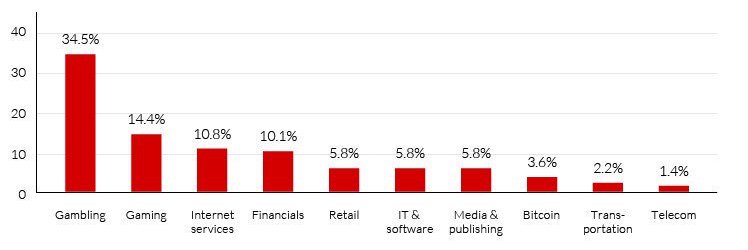
Such functionality is the hallmark of stresser/booter services that sell on-demand distributed denial-of-service attacks, which often attempt to overwhelm targeted sites with massive quantities of UDP and TCP packets. Stresser/booter services are regularly marketed on cybercrime forums and often used to disrupt gambling and gaming sites, cryptocurrency exchanges and financial services firms. Some forums, however, have banned the advertising of stresser/booter services, as HackForums did in 2016.
Top DDoS-Attacked Industries
Mirai's Legacy
Security researchers say Mirai was built by a group called PoodleCorp that apparently shared members with the infamous Lizard Squad DDoS gang. The malware targeted default or hardcoded credentials in dozens of internet-connected devices to take control of the devices and turn them into nodes in an attacker-controlled, widely distributed DDoS attack platform (see Teen Hacker Avoids Jail Over On-Demand DDoS Attacks).
Mirai's original purpose appeared to be to offer on-demand disruption of online gaming sites. In a likely attempt to throw investigators off of their trail, however, Mirai's creators in October 2016 appear to have publicly released the source code. Subsequently, multiple individuals or groups embraced the code and began using and refining it for their own attacks, including disruptions of Lloyds Banking Group and Barclays banks in Britain and an ISP in the West African coastal republic of Liberia, amongst many others (see Mirai Malware Attacker Extradited From Germany to UK).
Satori Clues: Amateur at Work
Satori is one of the latest iterations of Mirai. Check Point says that while the attack scenario - targeting a zero-day flaw in a widely used consumer device to launch large-scale DDoS attacks - might suggest that a nation-state or organized crime gang was involved, clues instead point to a less sophisticated actor.
"Surprisingly, it appeared an amateur threat actor under the nickname 'Nexus Zeta' seemed to be behind this new botnet creation attempt," the researchers say. "Indeed, he had recently been active in hacker forums seeking advice on how to build such an attack tool."
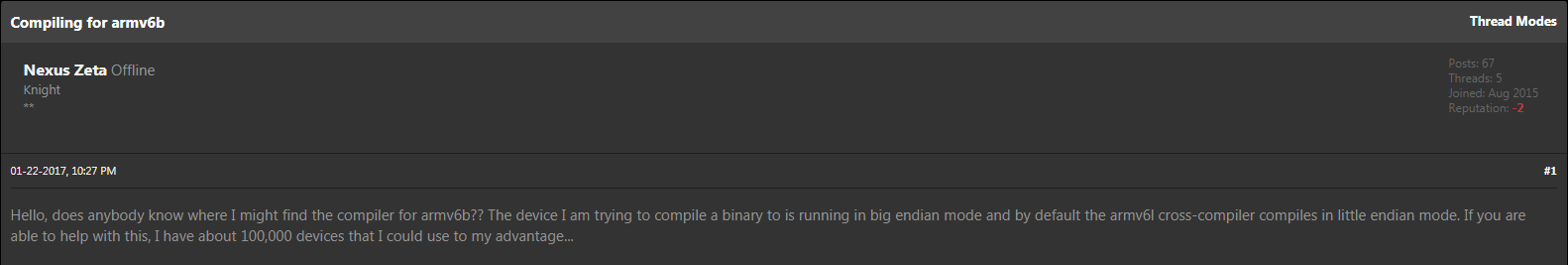
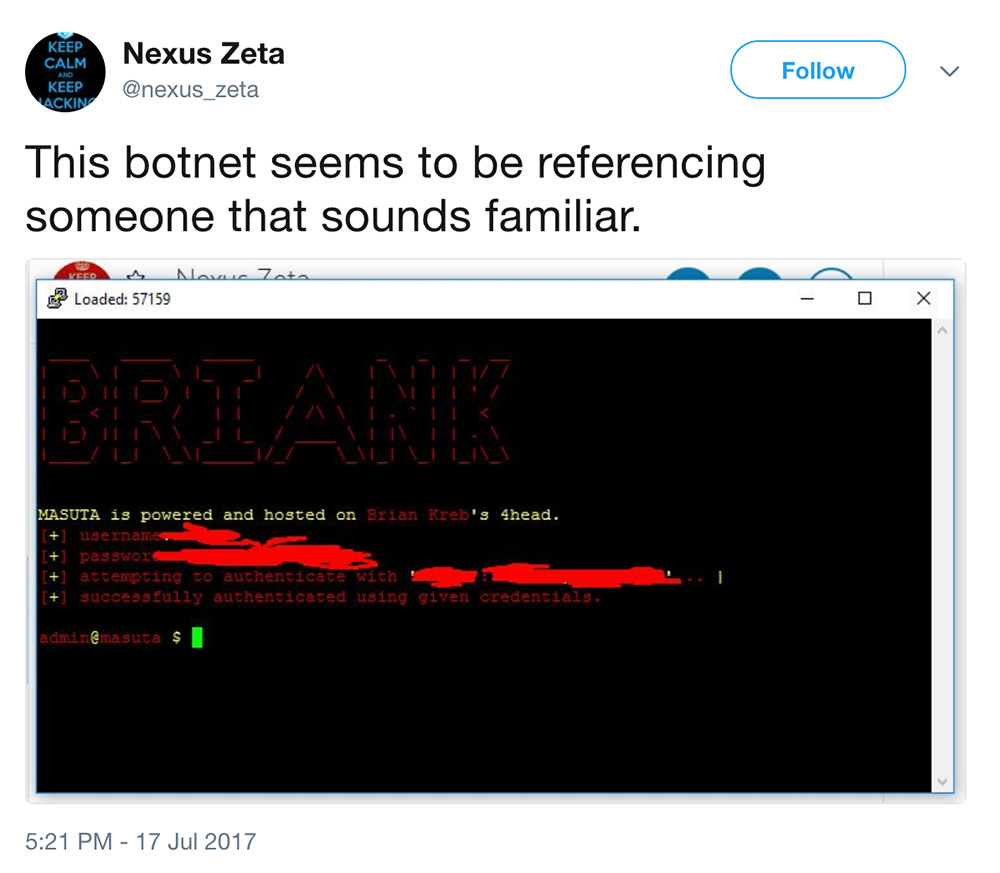
The Check Point researchers say that one of the command-and-control domains tied to Satori has been nexusiotsolutions.net, which was registered by someone using the email address nexuszeta1337@gmail.com; "1337" is hacker-speak for "leet," meaning elite. Searching HackForums, the researchers say they found a user account named "Nexus Zeta" that was registered in August 2015. Based on posts tied to the account, "his most recent focus was on an initiative to establish a Mirai-like IoT botnet."

The Check Point researchers add: "We also came across his Skype and SoundCloud accounts which are in the name of Caleb Wilson (caleb.wilson37 / Caleb Wilson 37), though it cannot be determined whether this is his real name."
Check Point says it's not clear how Nexus Zeta first learned about the flaw in Huawei HG532 devices.





















