Cybercrime , Cybercrime as-a-service , Fraud Management & Cybercrime
Fxmsp Hackers Behind AV Source Code Heist: Still Operating?
Remote-Access Vendor Promised to Make Buyers 'Invisible God of Networks'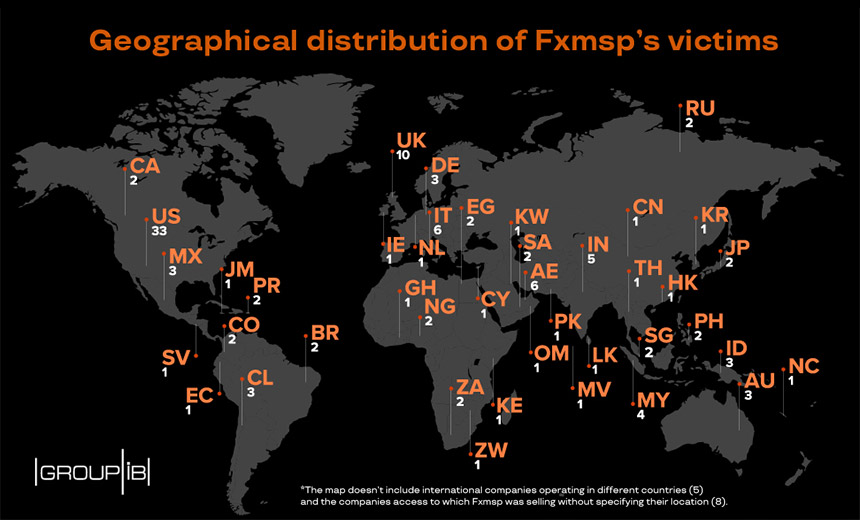
Is the Fxmsp hacking operation still in business?
See Also: The State of Organizations' Security Posture as of Q1 2018
In less than three years, security experts say, Fxmsp earned at least $1.5 million in illicit profits, largely driven by a botnet-based business model that enabled the group to sell remote access to other criminals (see timeline of group’s activities).
But Fxmsp gained widespread public attention in April 2019, after advertising - on underground forums - remote access to three anti-virus vendors' networks as well as 30 TB of stolen data, including source code.
In response, New York-based fraud prevention and risk management firm Advanced Intelligence, also known as AdvIntel, released a report into the Fxmsp hacking collective, which it says is led by an individual who might also use "Fxmsp" as their handle.
Designed to help law enforcement crack down on the gang's activities and potential victims to better prepare themselves, the report appeared to disrupt the group's operations, as well as those of its top affiliate, Lampeduza - aka Antony Moricone - by driving them off of the cybercrime forums they relied on for advertising their wares (see: Crime Gang Advertises Stolen 'Anti-Virus Source Code').
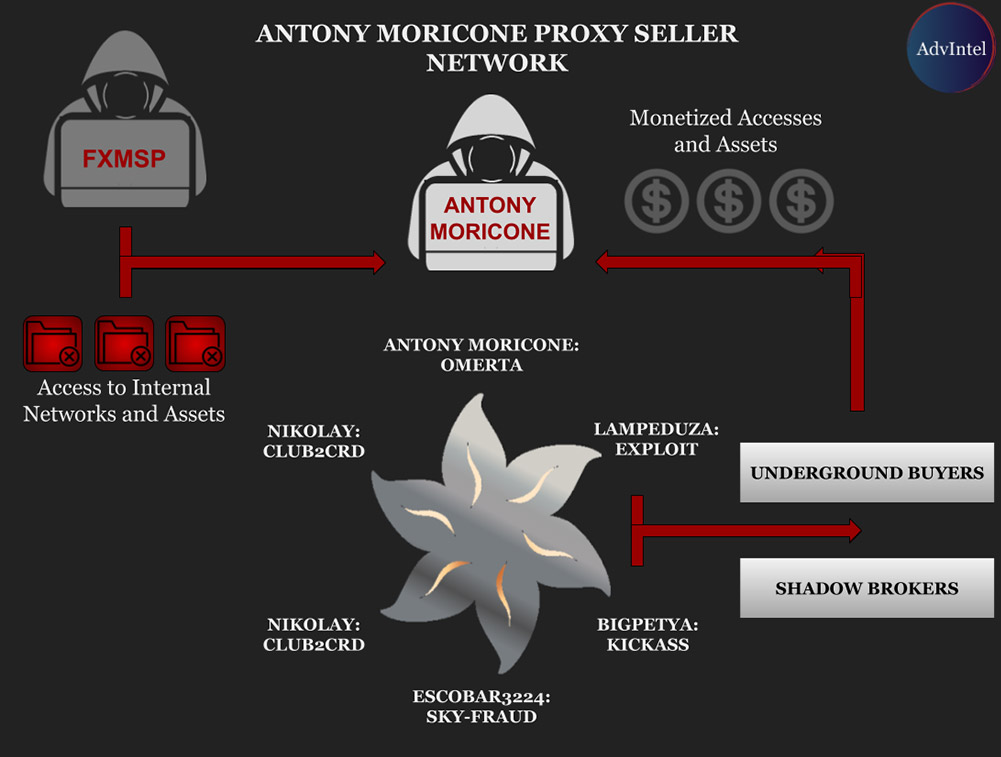
"Fxmsp disappeared from forums in October 2018, while Lampeduza" - the key affiliate also known as or partnered with Antony Moricone - "was still active until May 2019," Yelisey Boguslavskiy, AdvIntel's CEO, tells Information Security Media Group. "Fxmsp was acting privately - beyond forums - until May 9, 2019, when we terminated their operations."
Of course, members of the group may now be operating privately under different names. They would run the risk of drawing unwanted law enforcement scrutiny if they claimed to have worked with Fxmsp.
In a new report, Fxmsp: The invisible god of networks, Singapore-based cybersecurity firm Group-IB says there are signs that Fxmsp might still be at work. It found that "a European energy company that he was selling access to" - in 2018 - "fell victim to a ransomware attack in 2020." But of course, as Group-IB tells ISMG, that could be a coincidence.
Grand Unified Theory of Hacking
Reviewing Fxmsp's operations, Boguslavskiy says that thanks to the collective's "strategic vision," it clearly excelled at hacking.
"Fxmsp made an impression of being a very educated and talented person who had a clear dream of building an 'absolute exploit.' They wanted to perfect credential stealers and Trojans, make them as small and as invisible as possible, and they perceived it as being craftsmanship and art. But they did not plan to stop there," he says." They were fascinated by deepening the exploit framework, going beyond code structures, investigating vulnerabilities similar to Meltdown or Spectre, frequency hacking and hardware hacking."
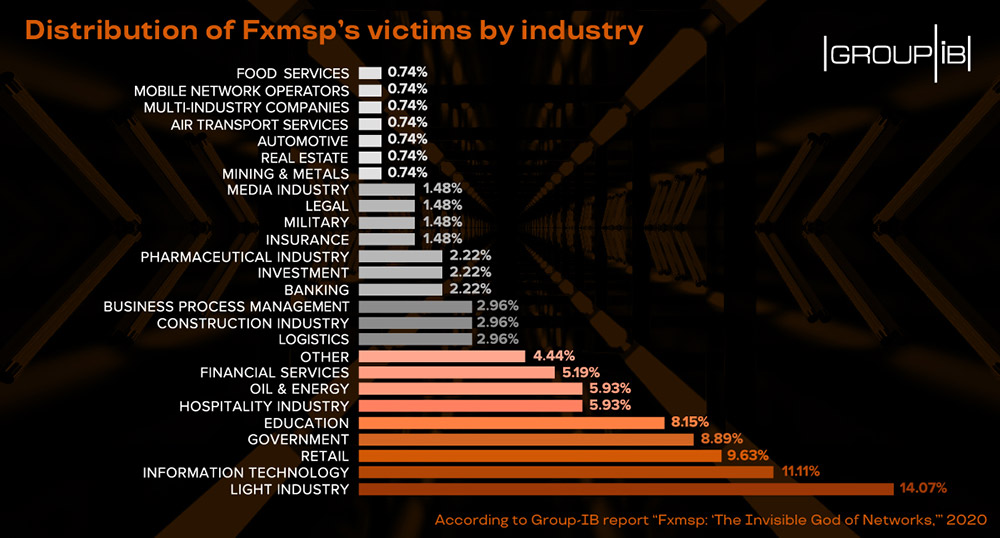
Hence, the group's disruption was notable, especially given that Fxmsp was a "big fish," having publicly advertised remote access to at least "135 companies, which brought him more $1.5 million in profits,” says Dmitry Volkov, CTO of Group-IB.
“He [the individual known as Fxmsp] set a trend and his success inspired many others to follow suit," Volkov adds. "Prior to Fxmsp joining the underground, sellers would offer RDP access to separate servers, without even bothering to ensure persistence or performing reconnaissance in the network. Fxmsp took this service to a whole new level."
Quick Rise
What might seem remarkable is that Fxmsp - the individual - appeared to first register for a Russian cybercrime forum in late 2016, with a query about how to monetize remote access to a network, as well as deploy Trojans and crypto-mining malware, Group-IB says.
By the summer of 2018, the group had earned a reputation for selling remote access to numerous networks of large organizations, including in the security and defense sectors. But the administrators complained that these efforts were disrupting a botnet they'd developed, via which the remote access appeared to be a side benefit.
"Fxmsp complained that they put too much time into processing the accesses and that they wish to stay more focused on the botnet development," Boguslavskiy says, noting that the botnet appeared to be "a credential stealer or a banker Trojan botnet."
3 AV Firms Allegedly Breached
The hacking collective's activities didn't come to widespread attention until April 2019, when Fxmsp sold what it claimed was anti-virus source code stolen from three vendors, which were later revealed to be McAfee, Trend Micro and Norton (Symantec). Fxmsp was also advertising remote access to all three vendors' networks, for a total price of $300,000. It's unclear if it had any buyers.
Symantec did not respond to requests for comment either at that time, or again this week.
At the time, both McAfee and Trend Micro confirmed to ISMG that they were investigating the claims.
“We have an active investigation underway related to recent claims, and while it is not complete, we want to transparently share what we have learned," a Trend Micro spokeswoman told ISMG in May 2019.
"At this moment, we are aware that unauthorized access had been made to a single testing lab network by a third party and some low-risk, debugging-related information was obtained," she said. "We are nearing the end of our investigation and at this time we have seen no indication that any customer data nor source code were accessed or exfiltrated. Immediate action was taken to quarantine the lab and additionally secure all corresponding environments."
McAfee had also confirmed it was investigating. "McAfee is aware of this threat claim targeting the industry," a spokesman told ISMG at the time. "We’ve taken necessary steps to monitor for and investigate it.”
Fxmsp's Breaches: Leftovers From Research
Boguslavskiy says one takeaway from the anti-virus vendor hacking was that it was a byproduct of Fxmsp's larger ambitions, which were to make their botnet tougher for security software to identify, as well as to successfully and automatically exfiltrate the greatest amount of data possible.
"In April 2019, Fxmsp stated that they had spent half a year online to investigate AV protocols, and this was their reason to attempt to breach Trend Micro, McAfee and Symantec," he says. "In this sense, the Fxmsp is not simply an audacious hacker who wanted to steal and sell AV data. Their collective acted in the best traditions of corporate espionage, in which they tried to steal source code to perfect and polish their own corporate offer - which was their botnet."
Boguslavskiy says this botnet-first ethos seemed to pervade everything the group did. "They investigated the compromised networks in order to see which other pieces of information they could automatically extract through their botnet," he says. "In other words, they acted as network intruders in order to increase the scale of botnet data exfiltration. The network intrusion was simply a side product of their botnet technology development efforts."
GameOver Zeus in the past, and the TrickBot gang currently, have used similar tactics, he notes (see: Emotet, Ryuk, TrickBot: 'Loader-Ransomware-Banker Trifecta').
Team Effort
Another key to Fxmsp's success was its well-organized group structure, including specialist divisions, which operated with a collective ethos akin to an international organized crime syndicate along the lines of the gangs behind GameOver Zeus or Andromeda, Boguslavskiy says.
"The Fxmsp claimed that they were a group divided into several divisions - in private conversations they always referred to themselves as 'we' or the 'team' and referenced 'our team people’," he says.
Key to some of its high-profile hacks, especially of government and financial networks, was a team of two hackers called "GPTitan," Boguslavskiy says. "GPTitan consisted of specialists who were geared to secretly work in financial environments. For $8,000 - $10,000 these hackers remained in a high-profile, breached network and extracted all the files which were relevant for the customers."
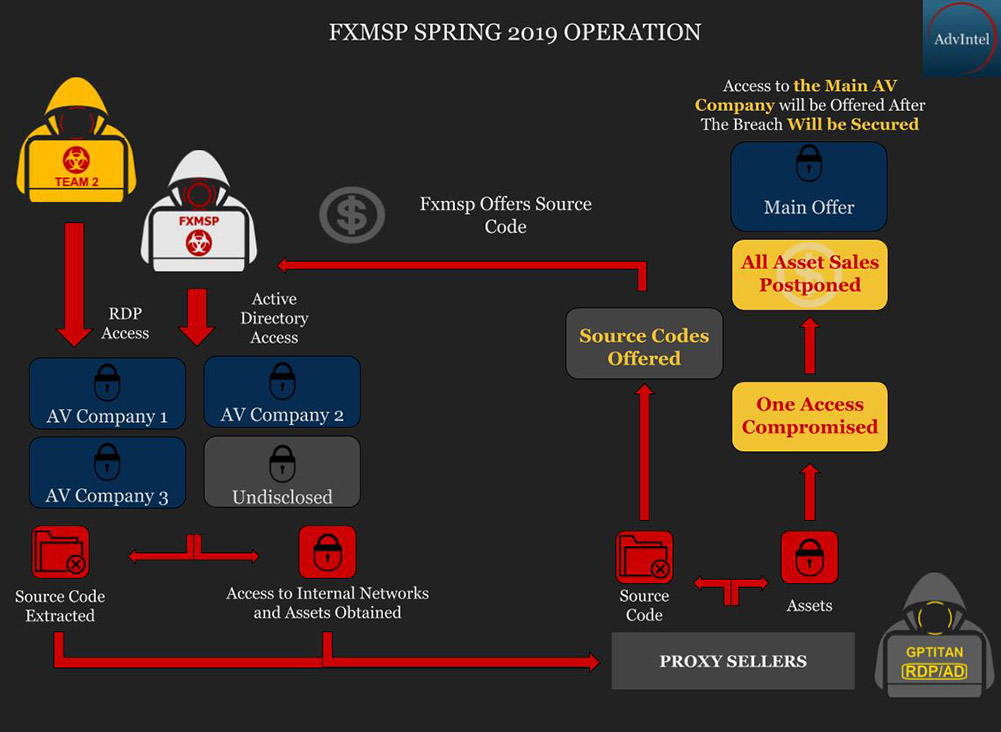
He adds that GPTitan was backed by two other teams - one based in China and another in the U.S. - and that "the collaborative effort of the three teams resulted in the spring 2019 anti-virus breaches."
Savvy Marketing
Another factor in the group's success was its ability to market, which it did via cybercrime markets, as well as privately via Jabber and Telegraph, often offering exclusive deals, according to AdvIntel.
"The Fxmsp hacking collective was explicitly reliant on the publicity of their offers in the dark market auctions and underground communities," Boguslavskiy says. "It is important to remember that processing and monetizing corporate access may present a way more significant challenge for hackers then even obtaining remote access to networks."
Fxmsp worked with the Antony Moricone group to help overcome this challenge and maintain a presence on both Russian-language as well as English-language forums. "Unlike numerous other Russian-speaking hackers who tend to focus on one jurisdiction, Antony Moricone offered corporate breaches for entities all across the globe thereby attacking targets in all possible geographies," he says. "They specialized in selling corporate data, internal assets and other crucial financial information."
Antony Moricone claimed to have nine years of experience working online, including four years in a startup setting, Boguslavskiy says. "They were an example of a pure, underground shadow broker weaponizing their knowledge of the corporate world to maximize Fxmsp's revenues on dark markets and shadow illicit actions via which corporate data is sold."
Gone From the Public Limelight
Given the risk potentially still posed by Fxmsp or its affiliates, Group-IB says it released its overview of what it knows about the group last week to "provide recommendations to help companies protect against the types of attacks conducted by Fxmsp and similar cybercriminals. We hope that our research will help to locate and arrest the threat actor hiding behind the nickname Fxmsp and his accomplices." The company adds that it has shared extensive details beyond what's in the public report -including the potential identity of Fxmsp's leader - with law enforcement.
Boguslavskiy suspects Fxmsp "may be still working privately using their botnet," or perhaps even joining forces with another botnet operation.
"The Fxmsp hacking collective was explicitly reliant on the publicity of their offers in the dark market auctions and underground communities. This is the main source of intelligence on Fxmsp's victims - the public postings on forums."
— Yelisey Boguslavskiy, CEO of AdvIntel
In addition, AdvIntel's research into political meddling and cybercrime turned up a high-profile threat actor - well-known on hacking forums as of December 2019, although now gone quiet - named b.wanted, who shares a number of similarities with Fxmsp. These include how the threat actor sounds in communications with buyers; the same focus on security and defense contractors; as well as the same sophisticated approach to always trying to obtain multiple ways of maintaining remote access into a breached network.
"It is likely that [b.wanted] is connected to the hacker collective Fxmsp," according to an AdvIntel report issued in December 2019. "For instance, b.wanted relies on a multilayered set of access backups, which includes botnet infection, access via credentials, access to the domain controller, and access via remote desktop protocol. These four types of accesses each secure the other - in case one method is being compromised, the other will still maintain the actor’s visibility into the victim’s network."
While overlap between the two personas has yet to be proven, "I personally believe that it is likely that b.wanted and the Fxmsp may be the same person, or members of the same team," Boguslavskiy says.





















