Access Management , Governance & Risk Management , Identity & Access Management
Democratic Campaign Group Left 6 Million Emails Exposed
UpGuard Finds Misconfigured Amazon S3 Bucket Left Addresses Exposed
A misconfigured Amazon Simple Storage Service database owned by the Democratic Senatorial Campaign Committee left more than 6 million email addresses of U.S. citizens exposed to the internet, according to new research from the security firm UpGuard.
See Also: OnDemand Panel Discussion | Practical Viewpoints: Global IT Security Compliance in 2022
The information within the Amazon S3 buckets dates back to at least 2010, although it's not clear how long the data had been left exposed or if anyone accessed it, the UpGuard team notes in a blog.
The UpGuard researchers first discovered the exposed Amazon S3 bucket on July 25. After researchers alerted the Democratic Senatorial Campaign Committee, the database was quickly secured, UpGuard reports.
Before the committee secured the database, the data within the S3 bucket could be viewed by anyone with a globally authenticated AWS user account. "This means that anyone with a free AWS account could access the bucket and its contents," according to the blog.
Over the last several months, UpGuard, along with other independent security researchers, have created a cottage industry of finding misconfigured, cloud-based databases exposed the internet. For example, UpGuard found 1 TB of data belonging to IT services firm Attunity left exposed (see: UpGuard: Unsecured Amazon S3 Buckets Exposed 1 TB of Data).
Clinton Ties
The UpGuard researchers first came across the Democratic committee’s exposed S3 bucket, which was named "toclinton," on July 25, according to the blog. The content of the bucket was a single zipfile with the name "EmailExcludeClinton.zip," UpGuard reports, and the permissions were set so that anyone with a free AWS account could view, download and modify the database.
The unprotected zip file contained a spreadsheet with over 6 million email addresses from major email providers, universities, government agencies and the military. The researchers found email addresses from almost all the major providers, including AOL, Yahoo, Hotmail, Gmail, MSN and Comcast.
In addition to these commercial email addresses, there were addresses associated with universities and schools. Plus, some 7,000 government email addresses and nearly 3,500 military addresses were included, according to UpGuard.
Purpose of Database Unknown
The exact purpose of the database is not clear, and it's not known why the Democratic committee was holding onto these addresses for over nine years.
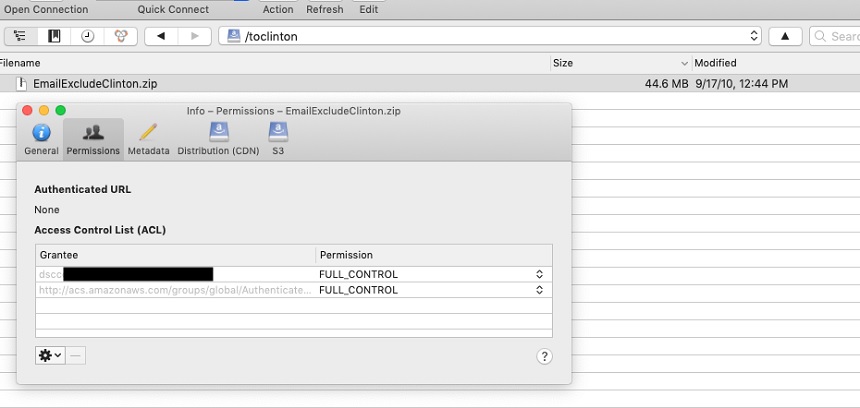
"The filename, 'EmailExcludeClinton.csv,' seems to indicate that this was a list of people who had opted out or should otherwise be excluded from DSCC marketing emails," according to the UpGuard analysis.
In addition, the UpGuard team points out that by 2010, Hillary Clinton was not running for any elected position. By that time, she had been confirmed as secretary of state for President Barrack Obama's administration; she didn’t run again for president until 2016.
The file with Clinton's name was uploaded to the Amazon bucket sometime in 2010 and was last modified in September of that year, UpGuard reports.
When the UpGuard researchers examined the permission set of the S3 bucket, they found a username that matched up to an individual who worked for the committee at that time who’s job was to add relevant data to the database.
The researchers note that email addresses can be valuable to a certain cybercriminals. "The same things that make this data valuable to political campaigns makes it valuable to malicious actors - intel on individuals that can be used to contact and influence them,” the blog states.
Growing Exposure of Political Data
Across the world, huge amounts of citizen data is being collected by political campaigns. But exposure of this data is becoming more common.
For example, on July 19, UpGuard researchers confirmed that a misconfigured database containing personal details of over 198 million U.S. voters was left exposed to the internet by a firm working on behalf of the Republican National Committee as part of their campaign efforts for President Donald Trump.
The exposed information included names, dates of birth, home addresses, phone numbers and voter registration details, as well as data described as "modeled" voter ethnicities and religions, according to the company's researchers.
S3 Buckets Under Scrutiny
The steady stream of data leaks and other security problems associated with S3 buckets is starting to draw politician attention of a different kind.
In July, when the FBI arrested a Seattle-area woman who allegedly compromised data belonging to Capital One, investigators found that she accessed an S3 bucket after entering the bank's network through a misconfigured firewall. It's not clear in this case if the cloud-based database was misconfigured, but Amazon is facing questions.
U.S. Sen. Ron Wyden, D-Oregon, has raised questions on security precautions taken by Amazon after the Capital One breach (see: More US Lawmakers Questioning Capital One, Amazon).