Fraud Management & Cybercrime , Governance & Risk Management , Incident & Breach Response
Cyber Ransom Group Hits Soft Targets: US Schools
FBI Pursues 'The Dark Overlord' as Group Escalates Extortion Tactics
For the past year and a half, a hacking group calling itself "The Dark Overlord" has struck businesses with weak cybersecurity defenses, hijacking their data and holding it for ransom.
See Also: 10 Incredible Ways You Can Be Hacked Through Email & How To Stop The Bad Guys
The group's approach relies largely on intimidation and embarrassment: Those that do not pay ransoms worth tens of thousands of dollars in bitcoin virtual cryptocurrency get taunted on Twitter. Eventually, the group often escalates to posting online sensitive personal information about people from within the targeted organization.
"This is cyber terrorism of sorts," says Nick Bilogorskiy, senior director of threat operations for security vendor Cyphort.
Other attention-seeking hacking groups have previously used the same tactics. But groups such as Anonymous and the Lizard Squad have faded away, thanks, in part, to law enforcement actions or members "aging out." Those hacking groups, however, appeared to pursue online hijinks less for money and more for notoriety.
The Dark Overlord wants both. The group, which is likely a very small collective who have never met in person, is under investigation by both the FBI and British authorities. Online identities related to the group have been traced back to Hell Forum, a notorious online gathering space in which cybercriminals shared attack tips. The forum is notable for being one of the places where stolen data from the Adult FriendFinder data breach appeared for sale.
But it has been difficult for law enforcement to track members of the group, which is exceedingly careful about not leaving digital clues that could divulge their identities, according to a person knowledgeable about the investigation.
Many of the group's attacks are staged from other hacked computers, which attackers subsequently wipe to erase digital forensic clues. Although sources say The Dark Overlord's hacking tactics are not particularly advanced, they've certainly appeared adequate enough to compromise organizations with weak defenses.
The Dark Overlord gained prominence around June 2016 when it began striking healthcare organizations. Since then, the group has ransacked health information systems, taking driver's license scans, medical records and even claiming to have stolen gigabytes of photos of labiaplasty procedures and gender reassignment surgeries.
But the attention being paid the group has heightened after it recently began harassing U.S. school districts. Such targeting is intentional; the group says that it is making an example of school districts to better compel high-tech companies from which they've stolen intellectual property to pay demanded ransoms.
Texted Threats
Recently, the Dark Overlord reached out to Information Security Media Group via encrypted instant messaging. Over the past week or so, ISMG and the group have been intermittently chatting. In the past, the group has approached a handful of information security journalists in an attempt to raise the profile of its escapades. ISMG is well aware of this tactic, because no one comes to a journalist for the benefit of the journalist. There's always an underlying motivation.
ISMG is also conscious of the potential downside of giving undue attention to cybercriminals who are actively seeking such attention. Given that the group has launched intimidation campaigns against several schools and that the FBI director has publicly addressed one of these situations, however, ISMG believes the group's campaigns merit the threshold for news coverage.
After hacking into school networks and stealing data on students, The Dark Overlord sent threatening notes to parents via text messages. The first such incident occurred in mid-September and led to the shutdown of 30 public and private schools in Montana's Columbia Falls School District for one week, affecting some 15,000 students, CBS News reported.
Against the backdrop of U.S. school shootings and violence, the group's threats triggered alarms, although authorities later determined that there was no physical threat. After the incident, Sen. Steve Daines, R-Mont., asked FBI Director Christopher Wray if he was aware of the threats, mentioning The Dark Overlord by name on Sept. 27 during a Senate Homeland Security and Governmental Affairs Committee hearing.
"Yes, Senator, we are actively involved in the matter that you're referring to in Montana," Wray responded. "I want to be careful not to discuss an ongoing investigation, but I will tell you that I could not agree more that this concept of ransomware, cyber terrorism, the various variants of it that are hitting, and I think the example in your state illustrates that it's everywhere now."
At the end of last month, the Dark Overlord ran the same type of harassment campaign against the Splendora Independent School District in Montgomery County, Texas. A spokeswoman for the district told local broadcaster KHOU that text messages and emails sent to parents and officials were "violent and graphic."
Officials there were unsure what type of data The Dark Overlord obtained, but it may have included students' names, phone numbers and addresses.
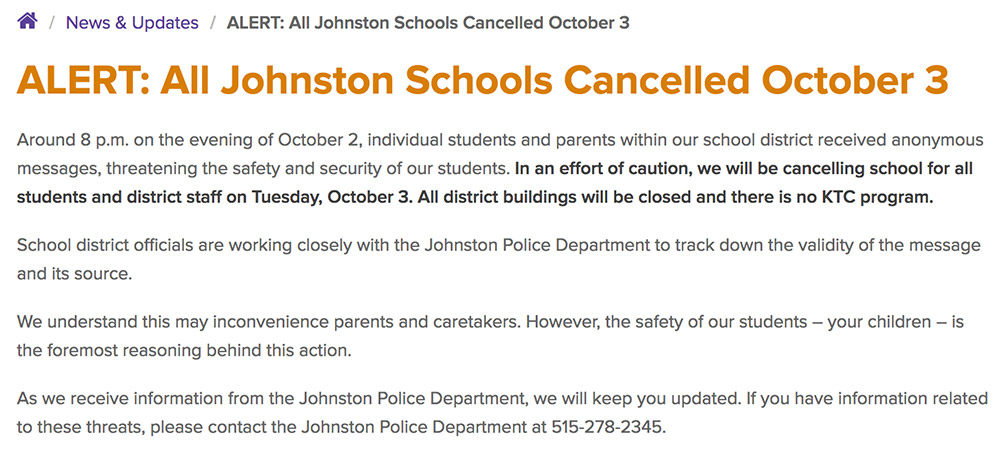
The group's subsequent victim, meanwhile, was Johnston Community School District in Johnston, Iowa. That campaign commenced Oct. 2, as ISMG was chatting online with a member of The Dark Overlord. The individual later sent recordings of people who'd been harassed and then phoned back the number from which the group sent threatening messages. As a result of those messages, the school district shut down classes on Oct. 3.
Schools might seem like poor targets for ransom schemes. Cash-strapped and ill equipped to defend their networked systems, schools are low-hanging fruit. But unlike businesses that might take it on the chin when their systems are hijacked by The Dark Overlord, schools have little recourse and only one mandate: to ensure that students are safe and to verify that they face no actual, physical threat.
'We're Sending a Message'
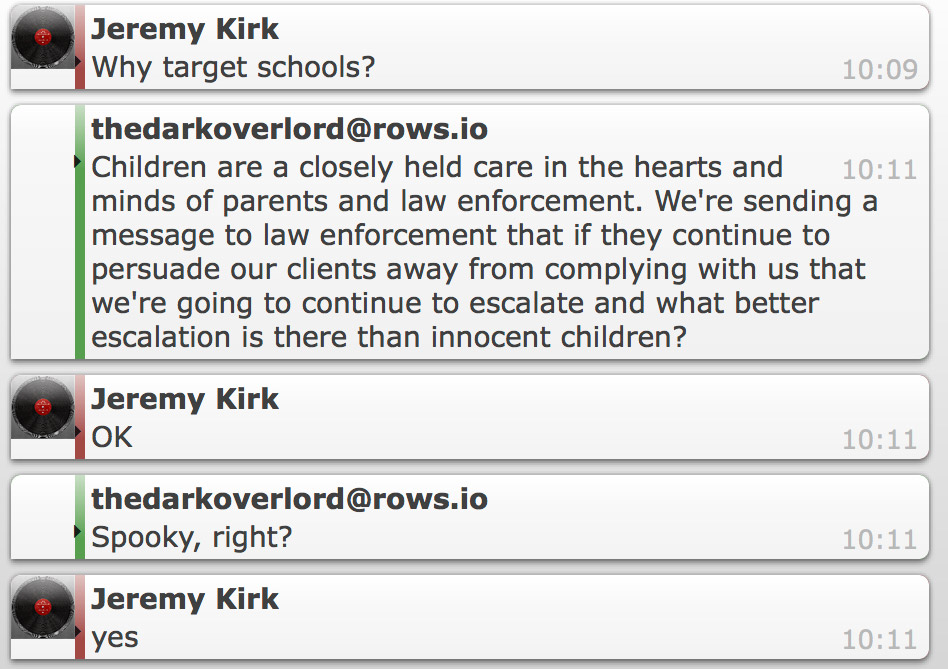
So why target schools? The Dark Overlord addressed on Tuesday via encrypted instant message.
"Children are a closely held care in the hearts and minds of parents and law enforcement," the group member writes. "We're sending a message to law enforcement that if they continue to persuade our clients away from complying with us that we're going to continue to escalate and what better escalation is there than innocent children?"
The group, in other words, does not shy away from using bold or intimidating language. Indeed, on Oct. 6, shortly after Johnston County School District shut down, The Dark Overlord tweeted: "With the student directory from JCSD we released, any child predator can now easily acquire new targets and even plan based on grade level."
With the student directory from JCSD we released, any child predator can now easily acquire new targets and even plan based on grade level.
— thedarkoverlord (@tdo_hackers) October 5, 2017
The Dark Overlord's stated rationale for targeting schools is that it sends a strong message to the dozens of businesses that they've hacked that they should pay the ransom. Such attacks remain ongoing. Within the last week, Dark Overlord demonstrated to ISMG that it apparently had stolen data from and been extorting both a shipping logistics company and a large Australian real estate company.
Hacker Contracts
When approaching a victim, the group typically sends a letter that mimics a genuine legal agreement and includes instructions about how to pay the ransom in bitcoins. If the money gets paid, The Dark Overlord agrees to let the matter end, without further consequences for the victim. On the last page of one agreement shared with ISMG, Adolf Hitler's signature is used in place of the group's own signature at the bottom of the document.

Despite the group's tactics, the FBI has long urged organizations to never pay ransoms. Victims that do pay not only fund future cybercrime, but may see criminals fail to honor the terms of the ransom agreement they dangled before the victim.
In one case that came to light earlier this year, the then-new season of the hit series "Orange is the New Black" was stolen from the systems of Larson Studios, a Hollywood post-production studio, and released online. One week after receiving The Dark Overlord's ransom note and 19 transactions later, the studio had paid the ransom, worth $50,000 in bitcoins, in full. At the same time, The Dark Overlord was trying to blackmail Netflix into also paying a ransom for the series to avoid it being released online, but Netflix rebuffed the extortion attempt (see Hollywood Studio Hit By Cyber Extortion Says: 'Don't Trust Hackers').
Subsequently, The Dark Overlord group dumped the episodes online, offering a faux-legalese rationale. "We found them to be in breach of contract," The Dark Overlord says. "You see, Larson Studios was not to cooperate with law enforcement as per our contract. However, Larson Studios cooperated with law enforcement in a manner that was in direct breach of our contract."