Business Continuity Management / Disaster Recovery , Fraud Management & Cybercrime , Fraud Risk Management
Connecticut City Pays Ransom After Crypto-Locking Attack
Separately, a Water Utility Hit by Ryuk Ransomware Vows to Restore, Not Pay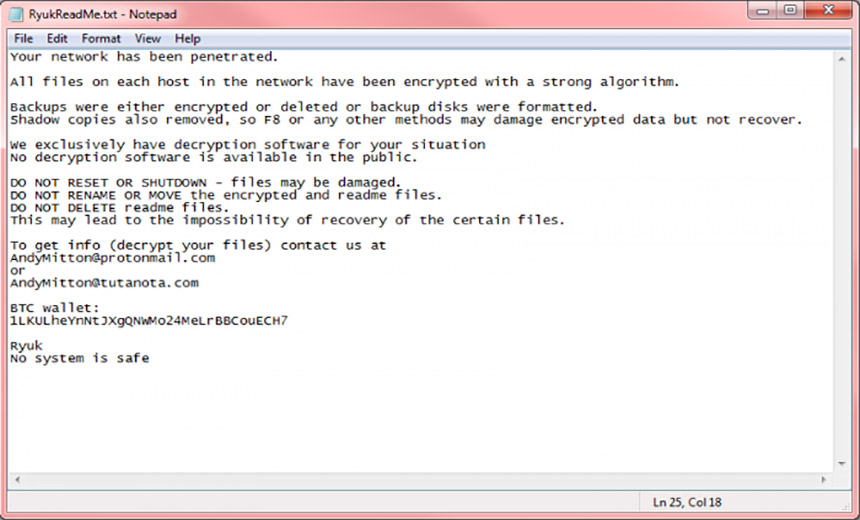
A tale of two different ransomware victims' responses: One town in Connecticut says it was left with little choice but to pay a ransom after attackers crypto-locked its systems. But a water utility in North Carolina, which was hit by a similar attack, says it will rebuild its systems rather than give attackers any money.
See Also: OnDemand | Strategies to Mitigate Cyberattack Risk in the 'New Normal'
In the Connecticut case, the city of West Haven reports that it was hit by a ransomware attack that ran from 2:49 a.m. to 3:16 a.m. on a Tuesday morning - Oct. 16. The attack infected 23 servers. The city says it had successfully contained the attack by 5:30 p.m. on Oct. 17.
Officials say the city's IT manager, David W. Richards, notified the mayor as well as local and national authorities about the attack as soon as it was discovered.
"MS-ISAC, a division of the U.S. Department of Homeland Security, assisted the West Haven Police Department in the investigation and determined the attack came from outside the U.S.," West Haven Mayor Nancy R. Rossi said in a statement released Thursday. MS-ISAC is the DHS information sharing and analysis center focused on improving cybersecurity for state, local, territory and tribal governments.
Rossi says the federal authorities, working with local police IT experts, "determined the best course of action, given all available information, was to pay a one-time fee of $2,000 to unlock the servers. The data restoration of a critical system occurred shortly after the completion of that transaction."
City attorney Lee Tiernan told the Associated Press that paying the ransom wasn't the city's first choice, but that after weighing all factors, it appeared to be the best approach.
City officials couldn't be immediately reached for comment about what type of ransomware crypto-locked their systems, or the virtual currency they used to pay attackers.
As of Monday, $2,000 was equivalent to 0.3 bitcoins or about 19 monero.
The city hired TBNG Consulting to provide incident response services as well as to help remediate and restore affected systems. "The response will be done methodically to reduce any future potential compromise," the mayor says.
"At this moment, there is no reason to believe that any data was stolen as a result of the attack, according to federal and local authorities," she says. "The attack remains under investigation by federal, state and local authorities, with local response being provided by TBNG Consulting."
Water Utility Attacked
News of the online attack against West Haven follows Onslow Water and Sewer Authority in Jacksonville, North Carolina, reporting that it was hit by an attack that began on Oct. 4, when Emotet malware infected its systems. The authority is a public, non-profit entity that provides water and sewer services to the unincorporated areas of the county as well as most local municipalities, serving more a population of more than 100,000.
Officials say the attackers appeared to deliberately target the authority with a two-stage attack after last month's Hurricane Florence.
"The [Emotet] virus was initially thought to be under control, but when it persisted, ONWASA brought in outside security specialists," the utility says. "The specialist continued to work the problem with ONWASA [IT] staff. At what may have been a timed event, the malware launched a sophisticated virus known as Ryuk at approximately 3 a.m. on Saturday, Oct. 13."
Ryuk is one of the hundreds of strains of ransomware, most of which are designed to forcibly encrypt data on a victim's PC or server and then demand a ransom in exchange for the promise of a working decryption key (see Obama-Themed Ransomware Also Mines for Monero).
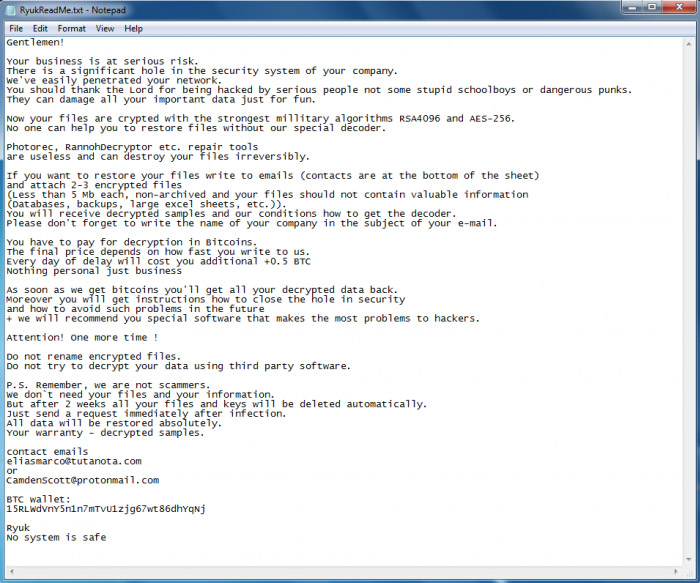
Ryuk ransomware was the subject of an Aug. 30 alert from the U.S. Department of Health and Human Services, which says the ransomware is often used in targeted attacks and distributed via phishing attacks. Like some other ransomware strains, the malware is designed to make it more difficult for victims to restore their systems (see Scotland's Arran Brewery Slammed by Dharma Bip Ransomware).
"At the end of encryption, Ryuk destroyed its encryption key and launched a BAT file that will remove shadow copies and various backup files from the disk," the HHS alert warns.
IT Staffer Saw Attack Unfold
Officials at North Carolina utility say an IT staff member working at the time that the Ryuk infections began at 3 a.m. on Oct. 13 witnessed what was happening and immediately began disconnecting systems from the internet, to no avail.
"The crypto-virus spread quickly along the network encrypting databases and files," ONWASA says. "The attack is similar in nature to those experienced by Atlanta ... and Mecklenburg County, North Carolina."
Mecklenburg County was hit in early December 2017 by a ransomware attack that disrupted government services. At the time, officials said they would not pay hackers the demanded $23,000 in ransom funds, but rather restore all of their systems from backups. "I am confident that our backup data is secure and we have the resources to fix this situation ourselves," County Manager Dena Diorio said at the time. "It will take time, but with patience and hard work, all of our systems will be back up and running as soon as possible."
ONWASA Vows Not to Pay
ONWASA, meanwhile, says it was compromised despite having extensive defenses in place. "ONWASA had multiple layers of computer protection in place, including firewalls and malware/anti-virus software," it says. "The defenses of the computer systems at the main office were penetrated."
"ONWASA will not negotiate with criminals nor bow to their demands. The FBI agrees that ransoms should not be paid."
It's not clear how the malware was introduced into the ONWASA's network, although the utility's description of the attack would be consistent with a phishing attack. But security experts say many Ryuk infections are the result of attackers either brute-forcing an organization's remote desktop protocol credentials or else purchasing stolen RDP credentials via cybercrime forums, to gain initial, remote access to a victim's network (see Locking Down PowerShell to Foil Attackers: 3 Essentials).
ONWASA says it has received one email from attackers - who it says may be located in a foreign country - containing a ransom demand.
Officials say that under no circumstances will they pay the ransom. "Ransom monies would be used to fund criminal, and perhaps terrorist activities in other countries," they say. "Furthermore, there is no expectation that payment of a ransom would forestall repeat attacks. ONWASA will not negotiate with criminals nor bow to their demands. The FBI agrees that ransoms should not be paid. ONWASA will undertake the painstaking process of rebuilding its databases and computer systems from the ground up."
The utility says no customer information was stolen. For at least a few weeks, the utility says that all plants and office locations will be operated manually, and it notes that no water or wastewater services have been interrupted. "While phone service remains, email service has been interrupted for most of the utility," it says.
Extortion Specialists
Security experts say that since then end of 2017, the growth in ransomware attacks has stalled. Instead, many criminals have begun focusing on cryptojacking, which involves mining for virtual currencies by stealing CPU power from victims.
Although ransomware attack growth has stalled, it still remains an oft-seen, illicit money-making tactic, and one of the top threats that the FBI says it's continuing to see. Likewise, the EU's law enforcement intelligence agency, Europol, says it continues to track extensive ransomware activity (see Cybercrime: 15 Top Threats and Trends).
"Healthcare, small utilities and municipalities are now the preferred targets for these extortion attacks," says information assurance expert William Hugh Murray in a recent email newsletter from SANS Institute.
"These attacks exploit the default access control rule of read/write/execute," he says. "Enterprise data should be stored only on servers with read-only or execute-only as the default access rules for most objects. Ransomware also requires a backup and restore capability that permits recovery of all data in hours."
Preparation Pays Off
The best way to deal with a ransomware infection is by preparing properly to safeguard against as well as rapidly recover from such an attack. Organizations that fail to do so face a difficult and expensive cleanup and restoration process (see Atlanta's Ransomware Cleanup Costs Hit $2.6 Million).
Alternatively, victims can pursue the ethically dubious choice of paying their attackers, who may not furnish a working decryption key.
Law enforcement officials say victims who pay often find themselves targeted again by the same or new cybercrime gangs. But they also acknowledge that the choice of whether to pay a ransom remains with victims (see Please Don't Pay Ransoms, FBI Urges).
While there are no official statistics for how many ransomware victims pay, obviously enough pay to keep ransomware gangs interested in continuing their efforts.
"As much as we tell people not to pay the ransom, people pay the ransom," FBI Special Agent Efrene G. Sakilayan, the bureau's assistant legal attaché to the U.K., told attendees at a Scottish cybersecurity conference in June (see 8 Highlights: Scottish 'Big Data' Cybersecurity Conference).






















