Fraud Management & Cybercrime , Incident & Breach Response , Managed Detection & Response (MDR)
Citrix Hacked by Password-Spraying Attackers, FBI Warns
Cyber-Espionage Campaign Appears Separate to Recent Credential-Stuffing Breach
Citrix Systems says it's investigating an apparent penetration of its network and theft of business documents by hackers. The technology giant, which is based in Fort Lauderdale, Florida, says it was alerted to the suspected intrusion on Wednesday by the FBI and that it has launched a digital forensic investigation.
See Also: What Mega Breaches Can Teach about Best Practices
"While our investigation is ongoing, based on what we know to date, it appears that the hackers may have accessed and downloaded business documents," Stan Black, Citrix's chief security and information officer, said in a Friday blog post. "The specific documents that may have been accessed, however, are currently unknown. At this time, there is no indication that the security of any Citrix product or service was compromised."
Citrix reported 2018 annual revenue of $3 billion. The company says its server, application and desktop virtualization, networking, software-as-a-service and cloud technologies are used by more than 400,000 organizations worldwide.
The FBI believes the technology company's network was penetrated using "password spraying," which refers to the tactic of attempting to remotely access a large number of accounts at once by using known usernames together with long lists of weak passwords, Black says.
"Once they gained a foothold with limited access, they worked to circumvent additional layers of security," he says.
Citrix tells Information Security Media Group that the breach does not appear to be connected to another hack-attack campaign that the company first disclosed on Feb. 15, in a form 10-K filing to the U.S. Securities and Exchange Commission.
"In late 2018, our file sync and sharing service was the target of a 'credential stuffing' attack, in which we believe that malicious third-party actors used credentials obtained from breaches unrelated to any Citrix service to attempt to gain access to individual Citrix Content Collaboration customer accounts," the Feb. 15 filing reads.
"To date, we believe the event had limited impact on a small percentage of Citrix Content Collaboration customers; however, these types of attacks have the potential to materially and adversely impact our customers and, as a result, our results of operations and financial condition," it adds.
Credential stuffing involves stealing passwords or obtaining lists of passwords from data dumps, and using them to access any other service for which a breach victim reused their same password (see: Credential Stuffing Attacks: How to Combat Reused Passwords).
Citrix says that the late 2018 attack appears to be distinct from the likely password-spraying attack that was the focus of the FBI's Wednesday warning to the technology firm. "Based on our investigation to date, we do not believe this matter bears any relationship to the credential-stuffing attack on our ShareFile service last year," spokeswoman Karen Master tells ISMG.
US Security Firm Blames Iranians
For the late-2018 credential-stuffing attack, cybersecurity and intelligence firm Resecurity, based in Los Angeles, said that Citrix was hit as part of a hacking campaign that it believes is being run by Iridium, which is its name for an advanced persistent threat group apparently operating from Iran. Resecurity says the attack campaign has hit more than 200 organizations, ranging from technology firms such as Cisco, to government agencies, defense contractors, financial services firms and oil and gas firms.
Resecurity says it originally warned Citrix on Dec. 28, 2018, that its network had been breached. "Based on the timing and further dynamics, the attack was planned and organized specifically during Christmas period," the company said in a Friday blog post.
"Based [on] our recent analysis, the threat actors leveraged a combination of tools, techniques and procedures (TTPs) allowing them to conduct targeted network intrusion to access at least 6 terabytes of sensitive data stored in the Citrix enterprise network, including email correspondence, files in network shares and other services used for project management and procurement," Resecurity said.
Resecurity's research suggests that Iridium's capabilities stretch beyond password spraying and include ways to bypass two-factor authentication. "The arsenal of Iridium includes proprietary techniques allowing to bypass 2FA authorization for critical applications and services for further unauthorized access to VPN [virtual private network] channels and SSO [single sign-on]," it says.
Attacks Against Parliaments
On Feb. 28, Resecurity said Iridium had been behind the recent, attempted breach of the Australian Parliament's network, which led to all lawmakers being required to reset their passwords (see: Hack Attack Breaches Australian Parliament Network).
Resecurity said it had tied the same group to a 2017 attack against the U.K. Parliament that compromised about 90 accounts (see: British Parliament Targeted by Brute-Force Email Hackers).
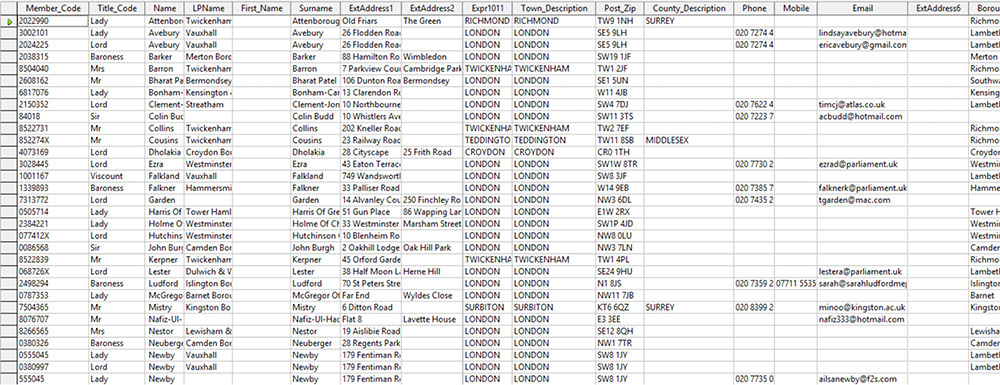
In December 2018, it said the group had successfully stolen data from the Liberal Democratic Party of London. The Lib Dems are the U.K.'s fourth largest party - after the Tories, Labour and Scottish National Party - holding 11 seats in parliament out of 650.
Supply Chain Attacks
Attackers' choice of Citrix as a target could mean that attackers were attempting to find a way to backdoor or otherwise compromise the company's products to give them a way to remotely hack into networks run by Citrix's customers.
In December 2018, for example, the U.S. Justice Department unsealed an indictment charging two Chinese nationals with being part of a nation-state hacking group called APT10, which allegedly perpetrated a cyber espionage campaign known as Cloud Hopper, in which attackers targeted IT managed service providers. By exploiting a single MSP, attackers could potentially gain access to the systems of its many customers (see: 2 Chinese Nationals Indicted for Cyber Espionage).
In 2017, meanwhile, NotPetya malware was spread by hackers who successfully infiltrated the software-updating servers used by M.E. Doc, which has 400,000 clients, including 80 percent of all businesses in Ukraine (see: NotPetya Patient Zero: Ukrainian Accounting Software Vendor).
But such attacks need not be the sole provenance of alleged state-sponsored groups. In 2016, for example, Oracle warned that its legacy MICROS point-of-sale systems had been breached, leading to security experts warning that hackers might have been able to easily distribute malware to such systems. At the time, POS systems built by MICROS were used at more than 330,000 locations, including hotels, across 180 countries. Security experts warned that 10 or more other POS vendors also appeared to have been targeted (see: Recent POS Attacks: Are They Linked?).
















