Fraud Management & Cybercrime , Governance & Risk Management , Next-Generation Technologies & Secure Development
Ethical Debate: OK to Pay Shadow Brokers for Exploit Dumps?
Goal of Crowdfunding by Security Researchers Is to Prevent Future WannaCrys
"Covfefe" is many people's word of the day, thanks to President Donald Trump apparently fat-fingering a Tuesday late-night tweet.
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
"Ethics," however, is the word of the day in the information security sphere, as the community debates whether it's acceptable to pay the exploit-leaking group known as the Shadow Brokers.
Debates rage after two researchers made that move, in the wake of Shadow Brokers promising to provide a first look at its monthly release of new exploits to anyone who pays a fee in a cryptocurrency called zcash. Currently, the fee being demanded - 100 zcash per month - is worth about $24,000.
Via the crowd-funding site Patreon, Matthew Hickey - cofounder and director of security firm Hacker House, based in Manchester, England - and the French security researcher known as X0rz, have launched an effort they've dubbed the Shadow Brokers Response Team.
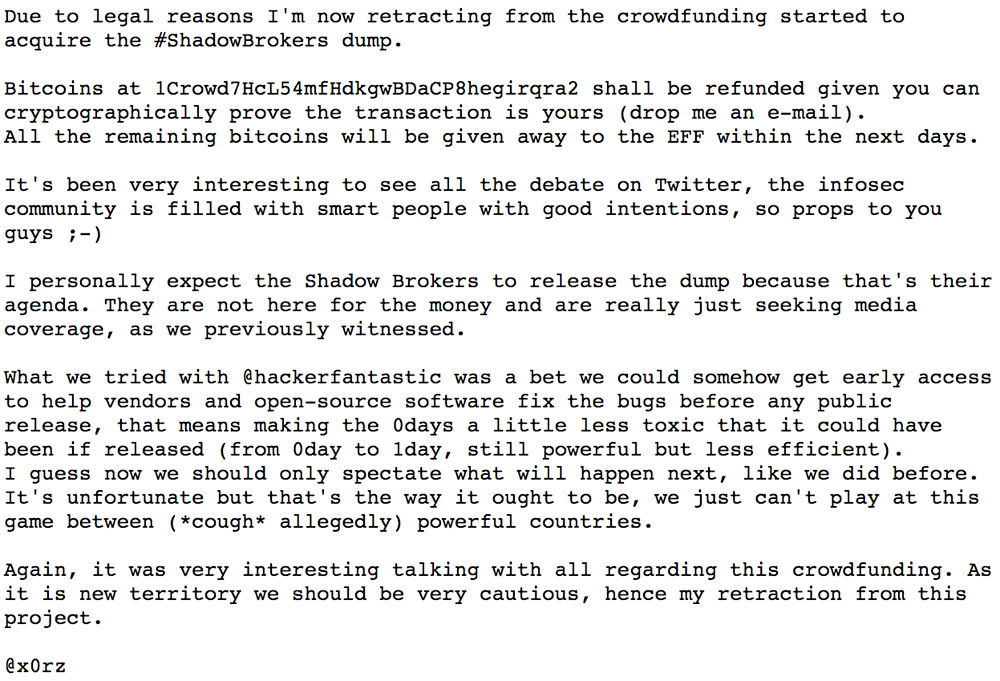
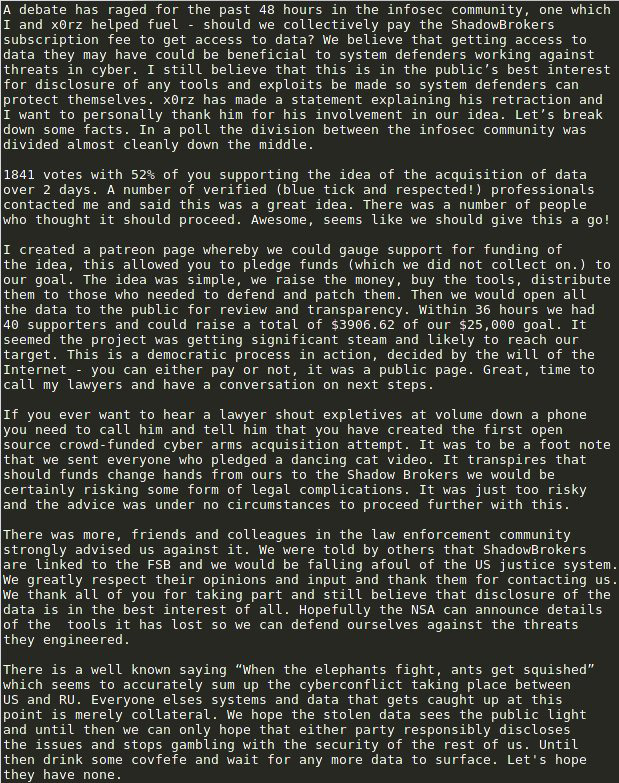
(June 1 update: Hickey and X0rz have called off their crowdfunding effort. See Canceled: Crowdfunding to Pay Shadow Brokers for Exploits.)
"The goal here is to raise sufficient funds from interested parties to purchase a subscription to the new data leak," the researchers write in their pitch, noting that the effort will be supported by three other well-known security researchers - Nicholas Weaver, Tarah M. Wheeler and Tim Strazzere.
Specifically, the researchers are looking to raise 100 zcash coins, purchase them from a reputable exchange, transfer then to the Shadow Brokers, hopefully get information back from the group, and then analyze that data and disclose it privately to affected organizations.
By Wednesday morning British Time, about a dozen backers had pledged $1,700.
"We will notify vendors and share data with any researchers who are involved," Hickey, who tweets as Hacker Fantastic, says via Twitter. "We will be expecting responsible disclosure practices."
#ShadowBrokers crowdfunding with @hackerfantastic, you can fund using 1Crowd7HcL54mfHdkgwBDaCP8hegirqra2 https://t.co/8iTBi0jtKM pic.twitter.com/3UuVormJ1K
— x0rz (@x0rz) May 30, 2017
Exploit of the Month Club
Shadow Brokers, which first set up online shop in August 2016, remains shrouded in mystery. Some speculate it may be a disgruntled U.S. government employee or a foreign intelligence agency. What is clear, however, is that the group has been leaking powerful attack tools, which it says originated with the Equation Group - a nickname for what security experts believe is the National Security Agency's network infiltration unit, called the Tailored Access Operations team.
Earlier this month, in a rambling online post, Shadow Brokers announced that they'd be launching an exploit-of-the-month service.
On Monday, Shadow Brokers drained its bitcoin account, and on Tuesday it released further details of its monthly dump service.
The terms: Anyone who sends 100 zcash, aka ZEC, by June 30 will receive a "mass email" sometime between July 1 and July 17 containing a link and password to obtain the group's June dump.
The group's pitch - written in the typical Shadow Brokers style, including rambling and difficult-to-read asides - makes no guarantees, claims or assurances about its offer, or its use of zcash.
"If you caring about loosing $20k+ Euro then not being for you," the offer reads. "Monthly dump is being for high rollers, hackers, security companies, OEMs, and governments. Playing 'the game' is involving risks. Zcash is having connections to USG (DARPA, DOD, John Hopkins) and Israel. Why USG is 'sponsoring' privacy version of bitcoin?"
Shadow Brokers had previously attempted to ransom exploits in return for a preset quantity of bitcoins, but saw an insufficient number of takers.
Follows WannaCry Worm
The monthly subscription offer follows Shadow Brokers having leaked in April an Equation Group attack tool called EternalBlue that targets a flaw in the Windows server messaging block. The flaw was used by unknown attackers earlier this month to launch an SMB-targeting worm designed to infect systems with WannaCry ransomware (see Teardown: WannaCry Ransomware).
Hickey tells me he sees paying the monthly subscription fee to be the least worst option for trying to blunt these types of devastating attacks in the future.
"Would I have paid £17,000 to stop the spread of WannaCry and keep the tools out of criminals hands? Absolutely," Hickey says.
NSA Could Come Clean
Ethically speaking, Hickey says the NSA could choose to undercut the Shadow Brokers subscription service.
"In an ideal world the [U.S.] government would make a statement about exactly what they developed and what they have lost, what is in the possession of blackhats and available to criminals so that we can defend against it," he tells me. "If they want to make that statement we will happily withdraw our attempt, however we are currently in the dark defending against adversaries whose tools are engineered by nation states."
To date, Shadow Brokers has released weaponized exploits that target technology from the likes of Cisco, Juniper, Linux, Microsoft Windows and Solaris.
Hickey, who launched a Twitter poll querying the community's response to the move, acknowledges that the subscription service may be a ruse. "They could of course have nothing at all, but if we do not attempt to at least find out then we cannot say we did everything in our power," he says.
Brave New World
Reaction from the information security community to Hickey and X0rz's move has been mixed. For some, it all sounds like a plot cooked up by dystopian science-fiction author William Gibson.
"Crowdfunding to buy nation state exploits from an anonymous group using untraceable cryptocurrency. The future got real cyberpunk real fast," says Brendan Dolan-Gavitt, an assistant professor at New York University, via Twitter.
In general, however, some information security professionals have come out in support of the plan, while others say they're against it.
"I'd rather form a team of uniquely talented folks to liberate the exploits back from SB and responsibly disclose all," information security professional Joe Harris says via Twitter in response to Hickey's poll.
Is a KickStarter project to pay Shadow Brokers subscription ($20k) and then perform analysis on it and responsible disclosure a good idea?
— Hacker Fantastic (@hackerfantastic) May 30, 2017
Some have disparaged the crowdfunding idea, and warned that it could put contributors at risk, legally speaking.
"If InfoSec vendors fund Shadow Brokers ($20k per monthly subscription) leaking Nation State tools I think it's a new low for InfoSec," says U.K.-based security researcher Kevin Beaumont, who tweets as Gossi the Dog. He called on the Equation Group, "whoever they may be," to instead responsibly disclose any and all stolen exploits still in their possession.
Crowd sourcing paying the Shadow Brokers is not my jam. It's indirectly funding crime.
— Kevin Beaumont (@GossiTheDog) May 30, 2017
There is a precedent for such moves. For example, Mike McNerney, a former Pentagon cybersecurity official, told the Washington Post that the NSA warned Microsoft about the SMB flaw in Windows after Shadow Brokers leaked the name of the Equation Group tool - EternalBlue - in January (see No Coincidence: Microsoft's Timely Equation Group Fixes). Microsoft released a related SMB fix for supported operating systems in March, after which the exploit was dumped in April. When WannaCry appeared May 12, Microsoft that same day released an emergency SMB patch for three unsupported operating systems: Microsoft XP, Windows Server 2003 and Windows 8.
It's not clear how many other patches from Microsoft and other vendors may already be due to information shared by the NSA or other intelligence firms.
Paying Thieves Encourages Theft
Alan Woodward, a computer science professor at the University of Surrey and a cybersecurity adviser to the EU's law enforcement intelligence agency, Europol, tells me that one of his chief concerns about the question of paying Shadow Brokers is that it "would encourage further such thefts, and so I'm afraid as much as I'd like to see what they have to say, I think it a poor idea."
Furthermore, it's not clear that any of this is actually about financial remuneration.
"I'm not convinced this is about the money. This group appears to be attempting to discredit the agencies it claims created the exploits," he says. "Look what happened when no one paid originally - they let it out anyway. It's really another form of ransom - even if someone does pay then there is no guarantee they won't just publish anyway."
He also voices ethical concerns. "I tend to work from a simple principle: criminals should not profit from their crime. I think this group is criminal - possibly politically motivated - and not some whistle-blowing vigilantes. Ergo, they shouldn't profit," Woodward says. "Maybe I'm being naïve but I worry that by a large number of people saying we'll all pay a little bit towards it, it could start to feel like a victimless crime."
June 1 update: Hickey and X0rz have canceled their crowdfunding effort. They issued the following statements:
Whatever happened to NSA warez crowd funding idea? Statement on why we pulled the plug on the opensource crowdfunded #ShadowBrokers purchase pic.twitter.com/5DRbu1KUdA
— Hacker Fantastic (@hackerfantastic) June 1, 2017