Business Continuity Management / Disaster Recovery , Fraud Management & Cybercrime , Governance & Risk Management
10 Ransomware Strains Being Used in Advanced Attacks
Advanced Hackers Continue to Linger in Breached Networks for Weeks or Months
Advanced attackers are continuing to camp out in networks for weeks or months, conducting reconnaissance and stealing sensitive data before unleashing crypto-locking malware.
See Also: Cybersecurity for the SMB: Steps to Improve Defenses on a Smaller Scale
Cybercrime researchers at Microsoft report that in the first two weeks of April, during the final stage of long-running attacks, they primarily saw cybercriminals wielding 10 strains of ransomware. They say that these gangs hit dozens of targets.
Despite the ongoing COVID-19 pandemic, healthcare sector organizations and their suppliers were not immune to such shakedowns (see: No COVID-19 Respite: Ransomware Keeps Pummeling Healthcare).
"So far the attacks have affected aid organizations, medical billing companies, manufacturing, transport, government institutions and educational software providers," Microsoft's Threat Protection Intelligence Team writes in a blog post.
Tactics: Smash-and-Grab, or More Advanced
Ransomware attacks can be categorized into one of two broad themes, says incident response expert David Stubley, who heads Edinburgh, Scotland-based security testing firm and consultancy 7 Elements.
"Each actor does what they want to do, but in the main, you've either got a smash-and-grab type of approach, where somebody has managed to get an end user to execute an executable that is the ransomware package in its own right ... or [the use of] malware to gain an initial foothold on a network, where they're not deploying the ransomware initially, they're doing it at a later date," Stubley says.
Smash-and-grab attacks may focus on one endpoint, for example, tricking victims into opening a malicious spreadsheet attached to an email, which, if opened, instantly begins encrypting every file on the system.
More advanced attackers, however, typically take their time before unleashing ransomware (see: Ransomware 2.0: Cybercrime Gangs Apply APT-Style Tactics). "Before that they're going to be doing network enumeration, credential theft and lateral movement, and some of the attack groups will be understanding what they compromised first before they head to ransom," Stubley tells Information Security Media Group.
10 Prevalent Ransomware Strains
Whatever strain of malware is used in more advanced attacks, they all unfold in broadly similar ways, experts say.
"Many of these attacks started with the exploitation of vulnerable internet-facing network devices; others used brute force to compromise [remote desktop protocol] servers," Microsoft says (see: Is COVID-19 Driving a Surge in Unsafe Remote Connectivity?). While different gangs used different tools and crypto-locking payloads, they all practiced relatively advanced network-penetration tactics.
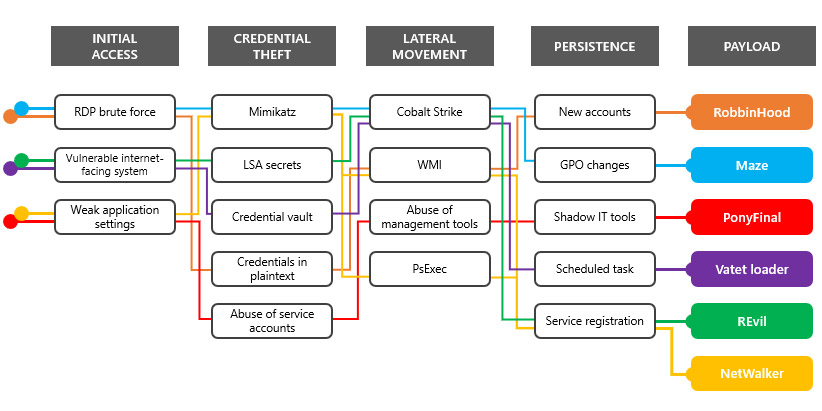
Microsoft says in the first two weeks of April, it saw sophisticated attacks get launched by gangs wielding the following types of ransomware.
- RobbinHood: "They typically start with an RDP brute-force attack against an exposed asset," Microsoft says. "They eventually obtain privileged credentials, mostly local administrator accounts with shared or common passwords, and service accounts with domain admin privileges. RobbinHood operators, like Ryuk and other well-publicized ransomware groups, leave behind new local and Active Directory user accounts, so they can regain access after their malware and tools have been removed." (See: Baltimore Ransomware Carnage Compounded by Local Storage.)
- Vatet loader: This custom loader is designed to work with the legitimate Cobalt Strike penetration testing framework, which is similar to Metasploit, and is being used by a gang that often brute-forces RDP endpoints or exploits CVE-2019-19781, a severe vulnerability in Citrix Application Deliver Controller and Gateway products that came to light last December and which Citrix patched in January (see: UK and US Security Agencies Sound COVID-19 Threat Alert). "The group behind this tool appears to be particularly intent on targeting hospitals, as well as aid organizations, insulin providers, medical device manufacturers and other critical verticals," Microsoft says. "They are one of the most prolific ransomware operators during this time and have caused dozens of cases."
- NetWalker: Attackers wielding this ransomware (also known as Mailto), have been hitting hospitals and healthcare providers using emails with COVID-19 themes that have malicious Virtual Basic scripts (.vbs) attached (see: COVID-19 Complication: Ransomware Keeps Hitting Healthcare). "The campaign operators also compromised networks using misconfigured IIS-based applications" to deploy the Mimikatz credential-stealing tool, use the PsExec command-line tool, and deploy NetWalker, Microsoft says.
- PonyFinal: While this ransomware might be Java-based, Microsoft says it's nevertheless being used to crypto-lock victims. "Campaign operators compromised internet-facing web systems and obtained privileged credentials," it says, followed by their establishing persistence and using Microsoft PowerShell to create a reverse shell for remote access. "They also used legitimate tools, such as Splashtop, to maintain remote desktop connections."
- Maze: The gang behind Maze gained notoriety in late 2019 for leaking stolen data in an attempt to force victims to pay. Many other gangs are now emulating this tactic (see: More Ransomware Gangs Join Data-Leaking Cult). The Maze gang also regularly targets managed service providers, so that by infecting one organization, they can potentially infect many more. Experts say Maze ransomware gets regularly spread via email as well as targeted attacks that begin via RDP, followed by attackers using Cobalt Strike, PsExec, PowerShell-based remote shells, Windows Remote Management and changes to Group Policy in Active Directory.
- Sodinokibi: The operators of this ransomware-as-a-service offering, also known as REvil, share ransom proceeds with affiliates actually infect endpoints. Some affiliates, inluding Maze, also specialize in hacking MSPs. Sodinokibi affiliates' "techniques overlap with many other groups, relying on credential theft tools like Mimikatz once in the network and performing lateral movement and reconnaissance with tools like PsExec," Microsoft says (see: Ryuk and Sodinokibi Surge as Ransom Payments Double).
Microsoft also says it saw the following four ransomware families being used in advanced attacks in the first two weeks of April.
- Paradise: Formerly distributed by email, Microsoft says this crypto-locking malware is now being used in more advanced attacks.
- RagnarLocker: This is installed onto victims' networks by a gang that relies on stealing credentials, deploying RDP and installing Cobalt Strike (see: Emotet, Ryuk, TrickBot: 'Loader-Ransomware-Banker Trifecta').
- MedusaLocker: This ransomware may be getting deployed by TrickBot infections, Microsoft says.
- LockBit: This ransomware is being used by attackers who also rely on CrackMapExec, a publicly available penetration testing tool, to move laterally across compromised networks.
Ransomware Often Trails Initial Breach
Microsoft says the more advanced ransomware outbreaks it's seen this month likely began with attackers compromising targeted networks several months ago. Since then, the gangs "have been waiting to monetize their attacks by deploying ransomware when they would see the most financial gain."
This is a typical modus operandi. "Groups activating acting weeks or months after compromise is not new behavior or nor is it unusual," Brett Callow, a threat analyst at security firm Emsisoft, tells ISMG.
According to FireEye's M-Trends 2020 incident response report, attackers camp out in a network for an average of 30 days before being discovered - if an internal security team finds them - or 141 days if an external source finds the breach.
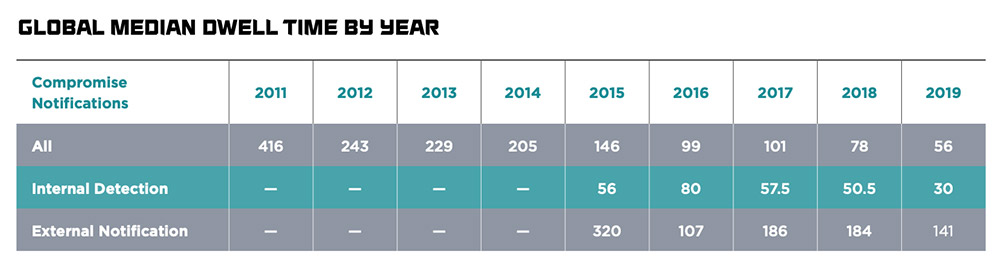
During that time, attackers typically ransack network-attached systems for valuable data, and as a monetization coup de grâce leave ransomware when they're done, 7 Elements' Stubley says.
For defenders, the imperative is clear, he says: Keep looking for signs that hackers have penetrated a network, so defenders can remove them and fix any flaws they may have exploited before the attackers have time to do more serious damage. "If you've already had a compromise, the odds are you've already got a reportable breach, which you already have to spend time and money investigating, and which is bad enough on a normal day," Stubley says. "But if you get to a point where you have to deal with ransomware as well, that's just shoveling on the pain."






















